Passwordless Authentication: The Fundamentals
Key Takeaways
- Passwordless authentication can reduce helpdesk calls by up to 33%, saving organizations thousands in support costs annually.
- With biometrics and possession-based factors, passwordless is nearly immune to phishing, a primary cause of data breaches.
- FIDO2 passkeys can work seamlessly across all devices in an ecosystem, offering both security and user convenience.
- Magic links and possession factors eliminate the risks tied to traditional knowledge-based authentication.
- Passwordless options are more than secure—they’re significantly improving user satisfaction by removing password frustration.
Passwordless authentication is a way of verifying a user’s identity without using a password. This type of authentication isn’t a specific type of technology, but rather, a goal or desired outcome.
The Problem With Passwords
Passwords are becoming outdated and are often the weakest link in protecting digital resources. Not only are they hard to remember, often reused on multiple sites, and need to be changed frequently, but for many IT departments, password support and maintenance are often their largest expense.
Is Passwordless Authentication Safe?
Replacing passwords with more secure authentication factors makes it much more difficult and expensive for attackers to be successful. For example, with FIDO (Fast Identity Online), the first open identity standard created to support passwordless authentication, user credentials never leave the device and are not stored on a server, which reduces vulnerabilities to phishing, password theft, and replay attacks. Additional authentication mechanisms, like risk signal tracking and device trust, make passwordless authentication methods even more secure.
But perhaps most importantly, passwordless authentication improves the user experience. Passwords present a host of usability problems that translate to poor experiences. It's much easier for users to provide a fingerprint or speak into a microphone than it is to remember and keep track of passwords. The best part is that much of the authentication process is done behind the scenes and users are blissfully unaware that it’s even happening.
What is Passwordless Authentication?
Passwordless authentication is a way to sign in to a digital account without the use of a password. In the world of access management, user authentication is performed using a variety of factors. A password is referred to as a “knowledge factor” because it is known by the user (as well as the server on the other end). The problem is that any time something is known, it is at risk of being shared inappropriately, stored insecurely, or stolen through phishing or malware.
These risks are eliminated with passwordless authentication.
With passwordless, instead of relying on something a user knows, authentication relies on something a user has (“possession factor”), like a mobile device, or something a user is (“inherence factor”), like a fingerprint.
Passwordless authentication offers key benefits to enterprises and users alike. It is better for security as it eliminates the risk associated with passwords, including the risk of interception in transit. It is better for the user experience because there is no password to remember and enter. And it’s better for the bottom line because it eliminates helpdesk calls for password resets and removes the IT burden of storing and securing passwords.
How Does a Passwordless System Work?
Passwordless authentication occurs when authentication factors other than passwords are used to access digital resources. One or more of these factors can be used:
- Inherence factors
- Possession factors
- Magic links
Note that passwordless authentication is not necessarily the same thing as multi-factor authentication (MFA). With multi-factor authentication, users are required to use two or more factors to prove that they are who they claim to be, and one of these factors could involve a passwordless authentication method. With passwordless authentication, users might be required to use only one factor, but that factor is not a password. If authentication requires more than one passwordless factor, it’s considered passwordless MFA.
Inherence Factors in Passwordless Authentication
Inherence factors — something you are — verify users’ identities with biological traits, such as fingerprints or retina scans, or behavioral traits, such as voice patterns and cursor movements. Users’ distinctive characteristics are captured, transformed into numerical data, and compared to data stored in a database. If this information matches the data in the database, users are granted access to the digital resource. On some devices, such as an iPhone, the fingerprint is stored on the device itself and is never shared or transmitted.
Biological Traits
Biological traits (also known as biometrics) provide an accurate way to verify a person’s identity using fingerprints, facial scans, and other “inherence” factors. They rarely change and they are difficult to replicate. This means that even if an attacker has a correct username and password, the attack will fail because there is no biological trait to carry out the intrusion. The use of biometrics makes digital transactions more secure and strengthens MFA by removing the leading cause of breaches: compromised login credentials.
Biometrics offer the added benefit of simplifying the user experience. After all, they are always available to the user and they eliminate the inconvenience of remembering passwords or entering codes sent to a mobile device.
Behavioral Traits
Behavioral traits, such as voice patterns, keystrokes, and gestures, can also be used to help verify a person’s identity. Many users are familiar with voice recognition technology, as it’s often used in banking applications as one form of identity verification. However, it’s rarely the only form, and it has become increasingly risky, as generative AI has made voice impersonation much easier for those seeking to commit fraud.
Other behavioral traits include the way users interact with their devices. Traits and gestures that can be tracked include the angle at which users hold their phones, the pressure they use on a touchscreen, or the speed of their keystrokes. As these interactions take place, data can be collected to provide a baseline about user behavior. Deviations in a user’s “normal” behavior can trigger the requirement for additional proof of one’s identity, also called step-up authentication.
Possession Factors in Passwordless Authentication
With possession factors — something users have — authentication occurs as users prove that their device is in their possession. The system sends a request for proof — it could be a one-time passcode sent via SMS (text message), a notification to the user's authenticator app, or a variety of other choices — and the user verifies possession to complete the login.
Public-key cryptography techniques can also be used for authentication, which involve cryptographic key pairs with public and private keys. You can think of a public key as a padlock and a private key as the key that unlocks it. All communications are encrypted and private keys never leave users’ devices, which lessens the chance of someone discovering them during transmission.
The introduction of the FIDO2 passkey
The FIDO passkey, introduced in 2022, is the latest digital credential that can be used for passwordless authentication. Based on standards by the Fast Identity Online (FIDO) Alliance and the World Wide Web Consortium (W3), passkeys represent a significant step forward in passwordless adoption, and many companies, including Apple, Google, and Microsoft have announced their support for passkeys.
One of the reasons passkeys are quickly catching on is that they’re phishing-resistant. There is no password exchanged between a user and a website, so there is no way to “intercept” a password in transit and no password to steal in a data breach. Passkeys are also convenient to use because they can work across most of a person's devices. That’s because, instead of storing the private key on the user’s device, it is stored in the device manufacturer’s cloud. So a user can register one device, such as an iPhone, and that user’s identity is connected through the Apple ecosystem, so the passkey can also be used with the user’s iPad and MacBook.
Magic Links in Passwordless Authentication
With magic links, users provide their email addresses during authentication and a unique token or code is created and stored. The identity system sends the user an email with a URL that contains this unique token or code. When the user clicks the link, the server verifies the token or code. Magic links can be set up for a single session or may be exchanged for a long-lived token (often stored as a browser cookie).
Generating and Sending Magic Links
With a magic link authentication process, a user visiting a website or trying to access an application is asked to enter an email address but not a password. If this email address is valid and associated with a customer or registered user, the application generates a unique, one-time link with an embedded token and sends it to the user via email. This token, associated with the user’s email address, is saved by the application. For security, the magic link will typically expire within a set timeframe.
Once the user opens the email and clicks the magic link, the application checks the token against the one generated by its server — if they match, the user is granted access to the given app or service.
Unique Tokens and Codes
By using unique tokens or codes that are associated with only one verified email address, magic links are more secure than one-time passcodes (OTPs) sent via SMS, particularly if the user’s email has MFA enabled. Magic links are also convenient, because the user doesn’t need to enter any verification codes — the website’s servers take care of that. And for security, once a user has signed in with a magic link, the token becomes invalid and cannot be reused.
Magic links have the added benefit of removing a significant burden from IT and security teams — managing and securing passwords — and they’re easy to set up using identity orchestration.
Benefits of Transitioning to Passwordless Authentication
The benefits of passwordless can be appreciated by anyone who’s ever interacted with a password, from IT security leaders to consumers with no IT experience whatsoever. Some of the benefits of passwordless are due to the fact that it
Requires no password for the user to create and remember
Provides a simpler registration and login experience
Delivers better security than passwords and resistance to identity attacks like phishing
Saves organizations money by eliminating helpdesk tickets related to password resets
- Prevents account lockout and shopping cart abandonment
Enhanced Security
Passwords are subject to a variety of password-based cyberattacks, including phishing and credential theft. Even the most rudimentary forms of attack, like brute-force and credential stuffing, remain highly effective because people continue to use passwords that are easy to remember, which makes them easy to guess. Worse, they use them for multiple accounts and rarely ever change them. For all these reasons, unauthorized access has been the leading cause of breaches for years — and that’s directly related to stolen usernames and passwords, which are regularly bought and sold on the dark web.
By eliminating the password, you eliminate all these threats. And because login credentials are never transmitted over the internet, there is no threat of interception.
User Convenience
Most people have dozens — if not hundreds — of online accounts that require passwords. If these passwords are appropriately complex, using random characters that spell nothing, people will not remember them. Forgotten passwords lead to password resets or account lockout, both of which are frustrating and time-consuming to correct. Many customers will leave a website rather than endure such a frustrating experience.
With passwordless, customers and employees can log in easily and conveniently with an email link, an authenticator app, or a method they’re probably already using daily, such as the face scan on their phones or Touch ID on their laptops.
Reduced Password-Related Support
Passwords are not just insecure, they’re expensive. It’s estimated that a third of helpdesk calls are related to password resets, and some estimates are even higher. A recent consumer study found that consumers’ top complaint about passwords is that they have too many to keep track of. This finding might explain why about a third of consumers say they must replace their passwords every six months and a quarter replace them every month due to forgetting or misplacing them.
Those resets aren’t free. Forrester Research estimated that each password reset was costing organizations roughly $70, and there’s little evidence that these costs are decreasing.
Compliance and Regulation
Organizations are under intense pressure to implement security measures that protect personal data in compliance with data protection regulations, such as the European Union’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), among many others.
Passwordless authentication can help in a few key ways. First, it significantly reduces the risk of password-related security incidents, such as phishing attacks and unauthorized access, which can expose sensitive data. Also, because passwordless requires no collection and storage of passwords, it reduces the amount of personal data organizations hold about their customers. The use of passwordless allows organizations to demonstrate to governing bodies that they are taking action to protect data and consumer privacy.
Tips for Adopting Passwordless Authentication
Start by Centralizing Your Authentication
Centralizing authentication with single sign-on and adaptive multi-factor authentication (MFA) provides the framework needed for passwordless authentication. Multi-factor authentication requires users to verify their identities using two or more authentication factors, while two-factor authentication (2FA) requires just two factors. Passwords are often used as the first authentication factor, but that is not a requirement for MFA or 2FA. Microsoft found that MFA can "prevent 99.9 percent of attacks on your accounts."
Authentication factors include:
- Knowledge = Something You Know (password, PIN, etc.)
- Possession = Something You Have (smartphone, key fob, etc.)
- Inherence = Something You Are (fingerprints, retinal scans, etc.)
A subset of Possession can be considered a fourth authentication factor by incorporating device-based behavioral and contextual information as "Something You Do." This new factor may look at the time of day a user typically logs in, usual location or behavior during sessions (keystrokes, speed, cut & paste frequency, etc.).
As we phase out the password, three stronger authentication factors remain for MFA and 2FA. Minimizing reliance on passwords not only makes your network more secure, but it reduces calls to your IT help center for password resets.
Adopt Risk-based Multi-Factor Authentication (MFA)
Risk-based MFA, also known as adaptive MFA, dynamically assesses the risk of a given interaction based on a variety of factors and adjusts the authentication process accordingly. By looking at the context and behavior of the login attempt, bad actors using compromised credentials can be stopped before they enter your system. For example, if a user is logging in from a suspicious IP address and trying to gain access to sensitive information, additional authentication methods can be required before access is granted. Failure to provide the additional proof will cause access to be denied.
By evaluating whether adequate security requirements have been met for each individual transaction and stepping up authentication when they haven't, an additional layer of security protects data without introducing unnecessary friction into the process.
Choose the Right Alternative Authentication Mechanism
There are numerous authentication methods that can be used instead of passwords. By providing a variety of authentication options, we can meet users how and where they prefer to work with brands and/or support different workforce scenarios.
The pros and cons of several of these methods are listed below.
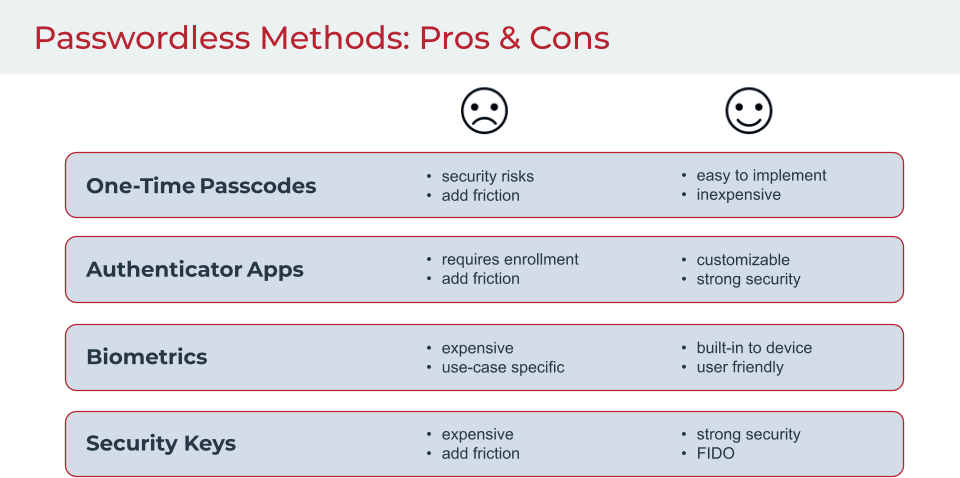
One-time passcodes (OTPs) fall into the Possession category, since OTPs are sent to a smartphone or generated by a device, such as a key fob, in the user's possession.
Authentication apps, such as Google authenticator or Microsoft authenticator, can be used to generate a one-time passcode for authentication.
Biometrics relate to unique physical traits. While many people are familiar with facial and fingerprint recognition, other forms of biometric authentication, such as retinal scans, voiceprints, brainwave and heart signatures, have been gaining prominence.
Security keys are hardware-based devices inserted into a computer or mobile device to grant the user instant access to services using a button or keypad.
Adopt Standards-based Authentication with FIDO and Public Key Cryptography
Numerous organizations have joined together to develop alternatives to passwords. Founded in 2013, the FIDO Alliance focuses on creating authentication standards to help reduce the world's reliance on passwords.
FIDO (Fast Identity Online) is a set of open, standardized authentication protocols that use standard public key cryptography techniques to secure user authentication. The fact that FIDO is an open standard means it is intended for widespread use, publicly available and free to adopt, implement and update. The standard provides advanced protection against phishing, man-in-the-middle and other common cyberattacks.
The FIDO Alliance published three sets of specifications, all based on public key cryptography:
- Universal Authentication Framework (UAF)
- Universal Second Factor (U2F)
- FIDO2
All communications are encrypted and private keys never leave the user's device, reducing the chances of someone discovering them during transmission. If biometric information is used for verification, it is also stored on users' devices, making these authentication processes stronger and more secure.
Users are able to sign on to a FIDO-enabled product or service using their preferred authentication method (fingerprint scan, entering a PIN, etc.) among the methods the product or service accepts.
You're Ready to Move to Passwordless
Start with the account creation process. Rather than using passwords during account creation, use a fingerprint scan or other authentication method. Identity proofing can also be part of your move to passwordless—at registration, during account recovery or at some other high risk event triggered by a signal. Having greater assurance that your users are who they say they are makes the transition to passwordless easier.
Usernames and passwords will become a thing of the past, along with the security issues associated with them. Eliminating passwords also eliminates the friction associated with creating, remembering and resetting passwords. Because more secure authentication methods already exist, the tools are currently available to reach your passwordless goal.
Passwordless authentication use cases
There are a variety of passwordless authentication methods and technologies available, and an infinite number of ways they can be used and combined to protect digital resources. Some methods are easy to implement and might be appropriate for accessing resources that do not contain sensitive information, while other methods provide robust security mechanisms but are more expensive to implement. All situations are unique.
For example, passwordless authentication methods are often used in the financial services industry due to the sensitivity of the data involved. In these two use cases, several different passwordless authentication methods are used to access account information.
Use case 1: Customer gift card balance access
To access a gift card balance, a retail company requires that users create a new account using their email address and password. The first time the customer accesses their account balance information from a new device:
- The system could email them a one-time authorization code, which they provide to obtain access.
- Or, the system could give the customer the opportunity to register the new device using a fingerprint, which they provide to obtain access.
Use case 2: Insurance adjuster record access
Additional security might be required to access more sensitive information. For example, if an insurance adjuster needs to access her client’s records, her identity could be authenticated using a variety of passwordless methods.
Authentication could involve sending a push notification to a phone-based authentication app, which uses fingerprint or facial recognition.
If for some reason, this method doesn’t work, a fallback authentication method, such as using a YubiKey could be used. Because the YubiKey is a FIDO authenticator and therefore not tied to a phone or laptop, the adjuster could use a PIN to unlock the authenticator and gain access. Security is maintained, and productivity isn’t negatively impacted.
To learn more about FIDO protocols and how they work, see FIDO (Fast Identity Online).
Conclusion
Organizations have tried for years to make the use of passwords more secure. They’ve required complex combinations of letters, numbers, and symbols, and they impose expiration dates. But these efforts create usability problems and add to helpdesk calls and account lockout. Worse, these passwords remain vulnerable because anything that’s “known” can be shared inappropriately or stolen. Despite efforts, the leading cause of breaches continues to be the unauthorized use of digital credentials, also known as passwords.
Passwordless authentication eliminates all the risks associated with passwords. Instead of relying on a user’s memory, passwordless authenticates users with something they have, like a phone, or something they are, such as a fingerprint. These methods are not only more secure, but they’re also more convenient to use, so your customers have no trouble accessing their accounts and your employees can quickly get to work. Passwordless also offers key bottom-line benefits by reducing helpdesk calls related to passwords, eliminating the need to manage and secure passwords, and preventing costly usability issues that drive customers to go elsewhere.
It's time to eliminate passwords once and for all, and it’s easier than you think. Learn about Passwordless Authentication Solutions from Ping Identity to explore the passwordless options that are right for your organization.
FAQs about Passwordless Authentication
Yes, it is generally more secure because it relies on factors like biometrics and device-based authentication, which are harder to compromise than passwords.
Absolutely. Passwordless systems often combine two or more factors like biometrics and possession factors, making them adaptable for MFA.
Financial services, healthcare, and retail, where high security and a smooth user experience are priorities, are primary adopters.
Systems usually have fallback authentication options, like push notifications, or secondary verification methods, to regain access.
FIDO (Fast Identity Online) is an open standard for passwordless authentication, providing secure and convenient methods that prevent credential theft.
Yes, it reduces support costs related to password resets and strengthens security, minimizing potential breach costs.
Start Today
Contact Sales
See how Ping can help you deliver secure employee, partner, and customer experiences in a rapidly evolving digital world.