Managing multiple tiers of identity can help boost brand management, yield security gains, and uncover revenue opportunities
Does the following sound anything like your organization? A complex, layered enterprise with many different business units (BUs). Inside these BUs are different departments. Inside of some of these departments exist different brands or products that need to be discretely managed to present unique digital experiences for customers.
If so, you are part of a growing cadre of organizations managing multi-brand experiences.
Traditional approaches to identity and access management (IAM) tend to break down when faced with these types of advanced multi-brand identity hierarchies. In the following paragraphs, I’ll explain why — and what you can do to prepare your organization for next-level success
Managing identity in a multi-brand environment
The term "multi-brand experience" fits neatly at the intersection of IAM and customer success.
On the IAM side, the challenge is granting the right users (internal workforce users and end-user customers) access to the right digital properties or assets needed to do their job or to complete their purchases — and in a timely manner
Take internal users. If too much access is given — for example, you grant users in Brand 4 access to resources in Brand 1 — you can unnecessarily and unwittingly expose part of the business to employees who do not need those resources to do their jobs. Worse, you can potentially open up a greater footprint of your business to hackers or malicious insiders.
On the customer success side, knowing a user is a consumer of Brand 5 leads to all sorts of interesting possibilities for going deeper on that interaction and the customer’s user experience. You can, for example, present a highly personalized shopping experience on that preferred brand or introduce a loyalty program for users of a particular brand. You can even strategically micro-target products and services that the consumer may be interested in. Or do both, why choose? The key is all about having an elegant, frictionless experience that starts with identity
“Customers” can also be internal workforce users requiring access to new applications and services. Being responsive to their needs in a timely fashion is critical for maintaining a productive and satisfied workforce.
Why delegated administration has failed to address the multi-brand challenge
The way organizations have traditionally attempted to handle multi-brand experiences is through the use of groups.
The logic goes like this: when you onboard internal users, the admin assigns them to one or more groups. For example, one user gets assigned to human resources, another to marketing, and another to finance.
Groups can cover the gambit, including location, projects, specialties, geography, and more. So, one user can be a member of the “Cleveland Plant” and another employee a member of the “Manchester Office.” Almost everyone is a member of multiple groups. Various admins (through delegated administration) then manage access to the groups, either allowing or denying the members of those groups access to various resources.
But then things get complicated. Companies grow, reorganize, and go through all manner of change over time, throwing the task of managing by groups and delegated administration into chaos. Groups are suddenly left without an admin. I have talked with customers who are managing up to 30,000 groups within their organization! Of course, nobody can actually manage 30,000 groups or do it well in any kind of fashion. What you end up with is the illusion of control without having any ability to drive the business forward.
The B2B2C business model (that is, business-to-business-to-customer) has moved to the fore. This means that multi-brand requirements now extend to business partners or vendors — intermediaries — who have contact with the end-user customers. Being able to control access to applications and services using this model, through the partner, and right on down to the end customer is imperative, and cannot be done effectively with groups and delegated admin
Addressing the multi-brand challenge with organizational model
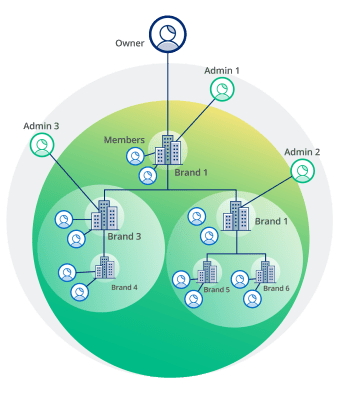
A better way to manage complex hierarchical identity requirements, including B2B2C, is through the use of an organizational model
An organizational model is first and foremost a data model. It is a structure that mirrors the actual organization itself (hence, the term “organizational model”). Rather than diving right into the typical IAM minutia of what groups, roles, and entitlements an individual user should be assigned to (all very important, by the way), an organizational model starts at the business level. By mirroring the way your business looks and operates, this model allows you to use identity more effectively and strategically to help the organization meet its business objectives.
An organizational model starts with a single organization, the top tier of the hierarchy. Then other organizational units (locations, brands, sub-groups, business units) can be flexibly built, assigned, and re-assigned across the organization as circumstances change. An almost infinite number of sub-organizations can be instantiated. Administrators are then assigned to each organizational unit, with the admins above having total visibility and control of other admins and members in the sub-orgs.
How does an organizational model differ from delegated administration? Here are a few differences (a non-exhaustive list)
- Utilization of non-technical admins – Typically, administrators need to have some IT and identity chops, or at least be part of the IT org. But with an organizational model, admins are presented with a simple portal to support access requests within their particular organization. This portal is convenient for assigning admin rights to a department owner who needs to make quick access decisions for direct reports. It also makes it possible to assign admin rights for onboarding users within a vendor, partner, or supplier.
- Supports full inheritance and visibility – Changes made to the top-level org, such as new access policies or authentication requirements, can automatically get pushed down to the sub-orgs without requiring admin intervention. This ensures that no group gets left behind, including B2B2C partners and vendors, when security decisions get made at the top. All access decisions are logged for visibility and assistance in passing audits and meeting compliance requirements down the road.
- Greater span of control – Who knows the access needs of users better than the application owner, business owner, or department head? An organizational model puts control into the hands of these users, while keeping IT in the driver’s seat. It can also speed decision-making.
- Better enforcement of least-privileged access – Rather than spraying broad access rights across the organization, members of each group are confined to just what is in their particular organizational area. In complex organizations with many BUs, this means reducing the surface area of a potential attack.
- Better support of a B2B2C model – In the past, extending access to partners and your partners’ customers was usually a one-off operation, with the necessary application sitting unmanaged within a department. With an organizational model, these projects are folded into the overall identity framework, meaning they are fully supported and secured within the same identity stack as the other users and applications.
ForgeRock delivers on the multi-brand experience
Increasingly, through acquisition and mergers, business restructuring, or even by legal and regulatory requirements, organizations are finding it necessary to manage different parts of their businesses like free-standing entities. ForgeRock Organizations supports your business by making your IAM mirror your organization, supporting complex B2B2C multi-brand initiatives, and covering both customers and internal workforce users from a single IAM platform. For more information, check out how we do this with ForgeRock Organizations.