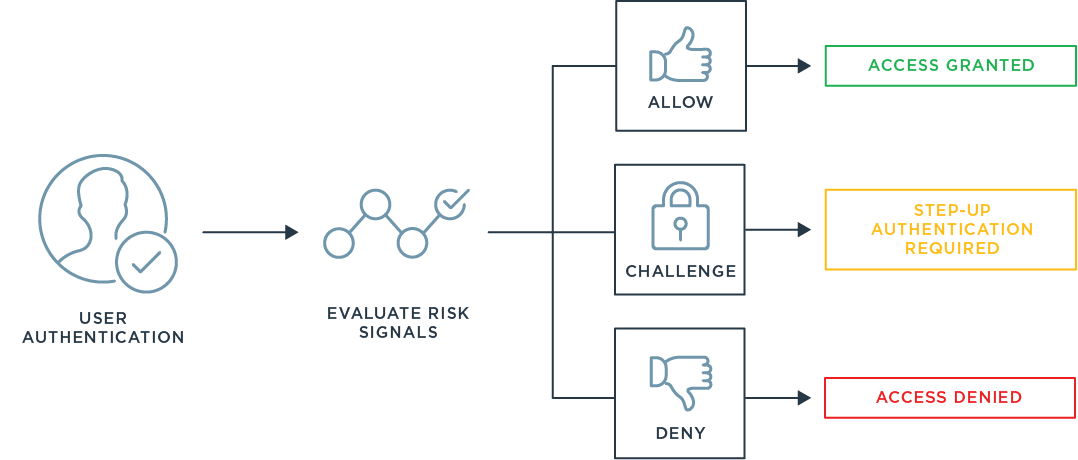
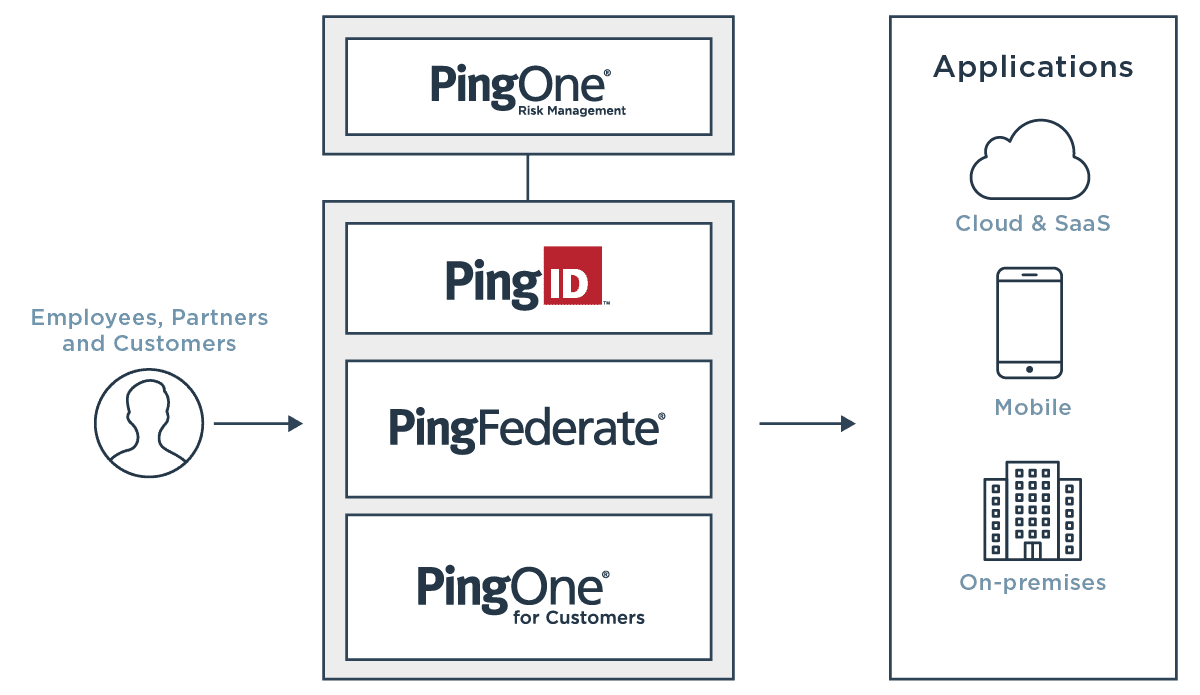
To address the growing number of risk signals, we recently released PingOne Risk, our cloud-based risk management service to enable organizations to analyze risk signals and detect anomalous behavior to make intelligent authentication decisions. PingOne Risk integrates with a variety of Ping products and third-party services to help organizations enable continuous adaptive authentication by analyzing risk predictors, aggregating risk signals into a single policy and providing in-depth dashboards for comprehensive security insights. Read on to learn about the four risk predictors available in PingOne Risk and how they can improve your security posture by providing insight into where risk is inside your organization.
1. User and Entity Behavior Analytics (UEBA)
Legitimate login attempts from employees and partners tend to follow predictable patterns, while login attempts from bad actors or hackers tend to deviate from the norm. Distinguishing typical login behavior from atypical behavior can help an organization identify the level of risk in an authentication attempt and block access to a malicious actor if needed.
To get the insight needed to distinguish between normal and anomalous behavior requires recording and connecting multiple data points about every authentication attempt in an organization. User and entity behavior analytics (UEBA) help you analyze requests to learn user behavior. These analytics can then be used to create intelligence-based policies and make smarter authentication decisions.
“By 2022, 60% of access management implementations will leverage user and entity behavior analytics capabilities and other controls to provide continuous authentication, authorization and online fraud detection.”
—Gartner Magic Quadrant for Access Management, 2019
Authentication policies created using UEBA leverage machine learning models that continuously analyze user activity to determine if the behavior is anomalous. These models take into account multiple variables of a user’s behavior to determine the level of risk the requester poses to the organization, including:
- Username
- Device type, operating system and version
- Browser type and version
- Date, time and location of authentication
If the risk level exceeds a certain threshold, malicious activity may be indicated. To block a potential attack, Ping customers can configure the policy to either step up authentication or deny access in this situation. Before applying the policy to the authentication flow for all users—and potentially introducing unnecessary friction—you can also use UEBA in evaluation mode to see the output of the machine learning model and adjust the policy rules as needed to deliver the right balance of security.
2. Anonymous Network Detection
Bad actors will typically rely on anonymous networks, such as unknown VPNs, TOR and proxies, to mask their IP address when attempting to breach protected, corporate resources. Historically, this incognito method has proven somewhat successful as it allows potential attackers to be untraceable when implementing an attack.
To prevent hackers or bad actors from using anonymous networks to gain entry to corporate systems, Ping customers can now apply a policy to analyze data from multiple sources about the address of the user requesting resources. If it’s determined that the user requesting access is coming from an anonymous network, you can apply a policy that requires the user to either re-authenticate or be denied access.
3. IP Reputation
Rogue actors often reuse IP addresses when conducting malicious actions like launching DDoS attacks or spam bots. So it stands to reason that if a user is requesting access to a resource using an IP address previously associated with suspicious activity, they may have malicious intent.
Using identity intelligence to analyze threat data, Ping customers can now evaluate the reputation of an IP address to better understand the risk associated with giving access, as well as determine the appropriate security action. For example, if a user logs in from an IP address where significant bot traffic has originated, they may be required to provide a stronger method of authentication. On the other hand, a user logging in from an IP address associated with online fraud might be denied access completely.
4. Impossible Travel
One way to identify potential malicious or fraudulent activity is to analyze changes in a user’s location. But in a dynamic and global business environment, users might log into services and applications from different countries in the course of a day.
Ping customers can now detect impossible travel situations by analyzing location data between logins and calculating the time it would take for the user to travel between the two locations. If the travel time is impossible, then a policy can be applied that requires the user to re-authenticate or be denied access. For example, if a user logs into an application in New York and then attempts to log in from Moscow an hour later, they can be prompted to provide a stronger authentication method or be denied access altogether, depending on how the policy is configured.