New capabilities fix security issues with MFA push notifications
Zero Trust security models call for the use of multi-factor authentication (MFA) to ensure that only authorized users may access protected IT resources. Many organizations are adopting MFA to add a layer of security for remote workers. Customer-facing organizations are also implementing MFA to mitigate identity-based attacks, such as phishing, and to help quash the rise in account takeover fraud.
For five consecutive years, the leading cause of breaches has been compromised credentials — in other words, the use of stolen passwords. MFA renders the use of stolen credentials futile, as attackers are highly unlikely to have access to a user's other authentication factors, such as a mobile phone.
Microsoft has stated that using MFA may stop 99% of password-related attacks within an enterprise, so an increasing number of enterprises have begun to require MFA before granting account access. That's the good news. The bad news is that attackers are now trying to undermine the effectiveness of MFA with some success.
MFA is under attack
While MFA is a vast improvement over a simple username and password combination, there are ways that MFA can be compromised, including:
Man-in-the-middle (MitM) attacks: Fraudsters position themselves between organizations (such as financial institutions) and users to intercept, edit, send, and receive communications without being noticed.
SIM-card swapping attacks: A cybercriminal uses social engineering tactics to transfer a user's mobile phone number to a new SIM card owned by the criminal. If such an attack is successful, the victim's apps, including banking apps, can be activated on the impersonator's phone.
Pass-the-cookie attacks: A session or authentication cookie can be stolen and injected into a new web session to trick the browser into thinking the authenticated user is present and does not need to prove their identity.
MFA fatigue attacks (aka MFA spamming or MFA prompt bombing): The MFA fatigue attack relies on people to be distracted, careless, or frustrated by frequent requests to authenticate. As a new form of social engineering, MFA fatigue raises considerable security concerns.
What is MFA fatigue?
Sometimes, as a means to an end, people will engage in behavior that they know is borderline unsafe. Who amongst us hasn't disabled a smoke alarm to make the low-battery alert stop its intermittent screeching? MFA fatigue attacks rely on similar human impulses, which ultimately make users vulnerable to schemes such as MFA prompt bombing.
With MFA prompt bombing, attackers attempt to get access to an account or device by flooding a user's authentication app with push notifications. Some attackers send a few push notifications a day thinking they will fly under the radar, while others bombard the user with continuous messages, but the intended outcome in either approach is the same: to get users to authorize access in order to make the notifications stop, thereby granting access to the attacker.
Preventing MFA attacks
Push authentication is one of the most secure, simple, and convenient user authentication methods and a popular MFA choice. To avoid attacks on push notifications, ForgeRock has developed two features: MFA push authentication with context and push authentication with number matching.
Push notification with additional context
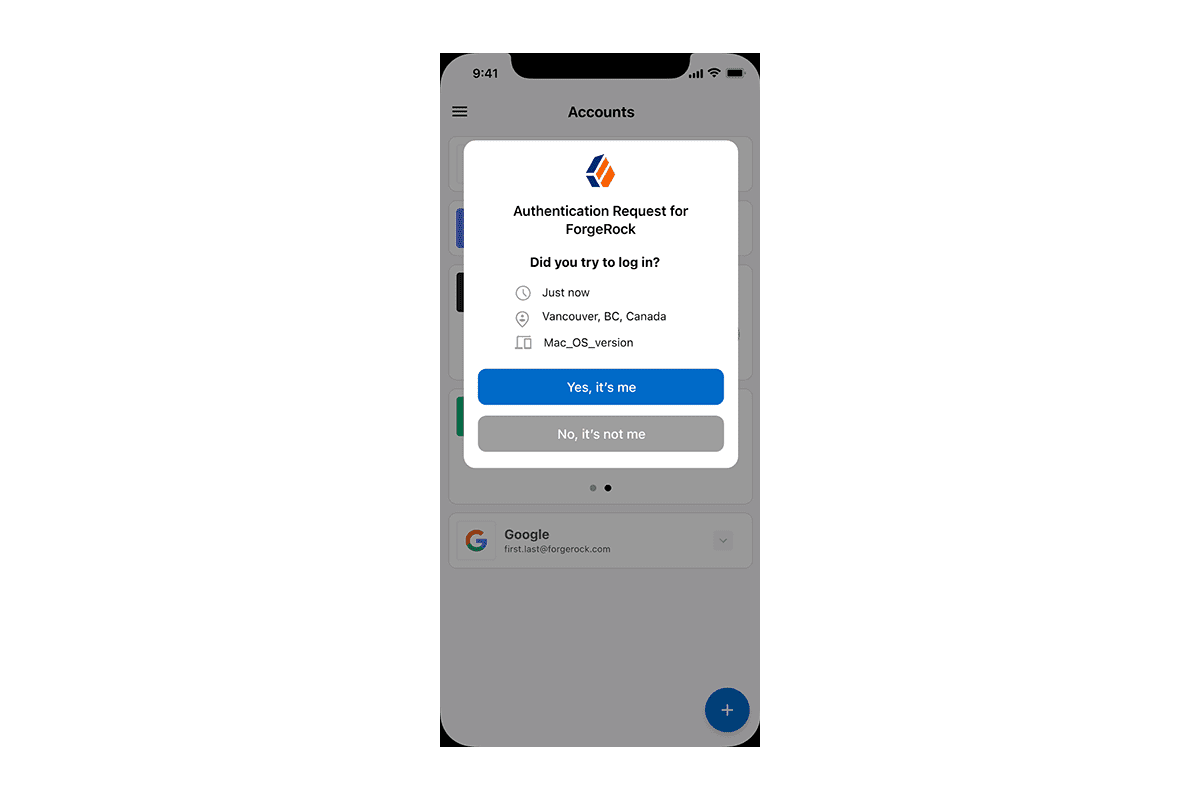
The push notification with context feature lets you keep your users safe from MFA attacks by sending them additional context. When users are presented with a push notification request, they are provided contextual information about the request, such as where the request came from, information about the device, the user agent, or other signals.
When the push notification is received, the user can review the contextual authentication information, decide whether it is legitimate, and accept it or reject it.
Push notification with number matching
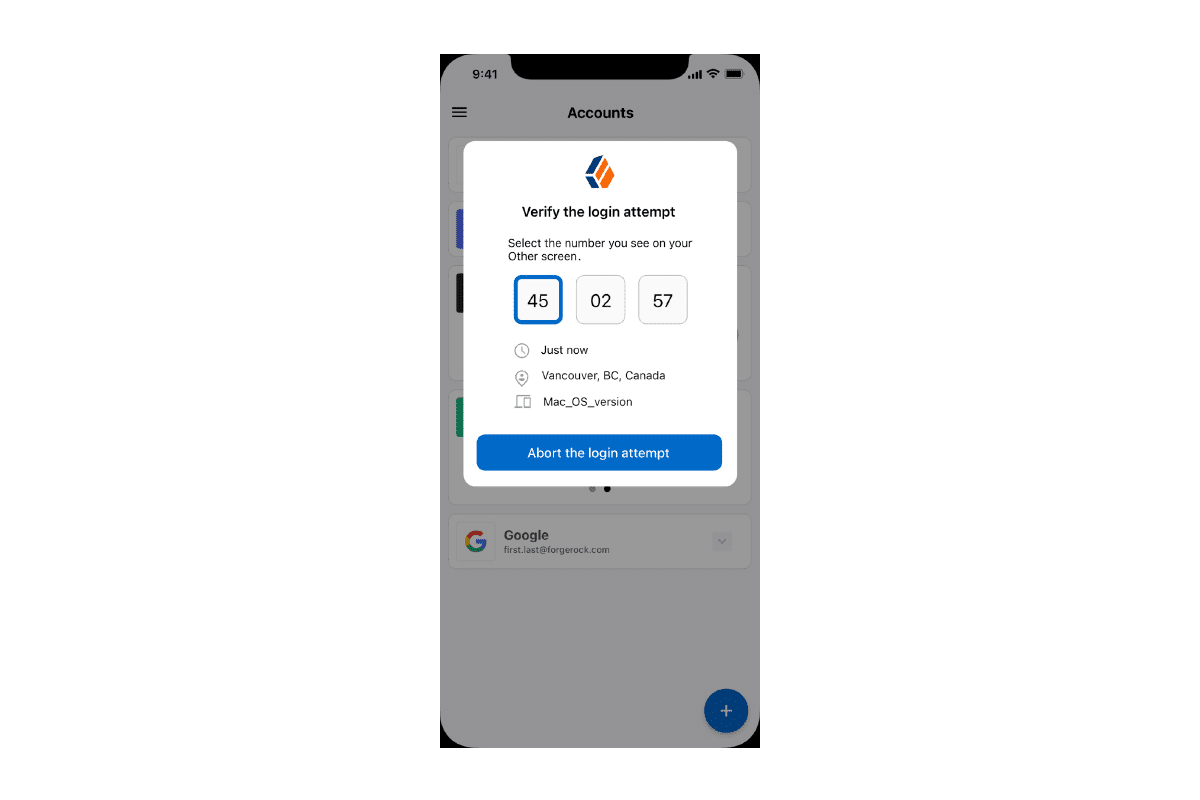
With number matching in a push request, the user is presented with a number on the login screen and must select that same number in the authenticator app.
For more secure logins in the near term, we advise enabling push notifications with number matching. This method prevents an attacker from gaining access to an account if the user accidentally hits "Approve" on an MFA notice.
This technique also minimizes friction for users. When compared to other MFA techniques, such as entering a six-digit number from a software token or SMS message, matching a two-digit code doesn't significantly add to the login process.
Why enterprises should use these MFA approaches
If you've implemented MFA using an authenticator app for your workforce users or your customers, you want to be sure it isn't vulnerable to MFA fatigue. With the ForgeRock Authenticator's additional context or number matching, you will no longer have to worry about users who unintentionally approve MFA requests.