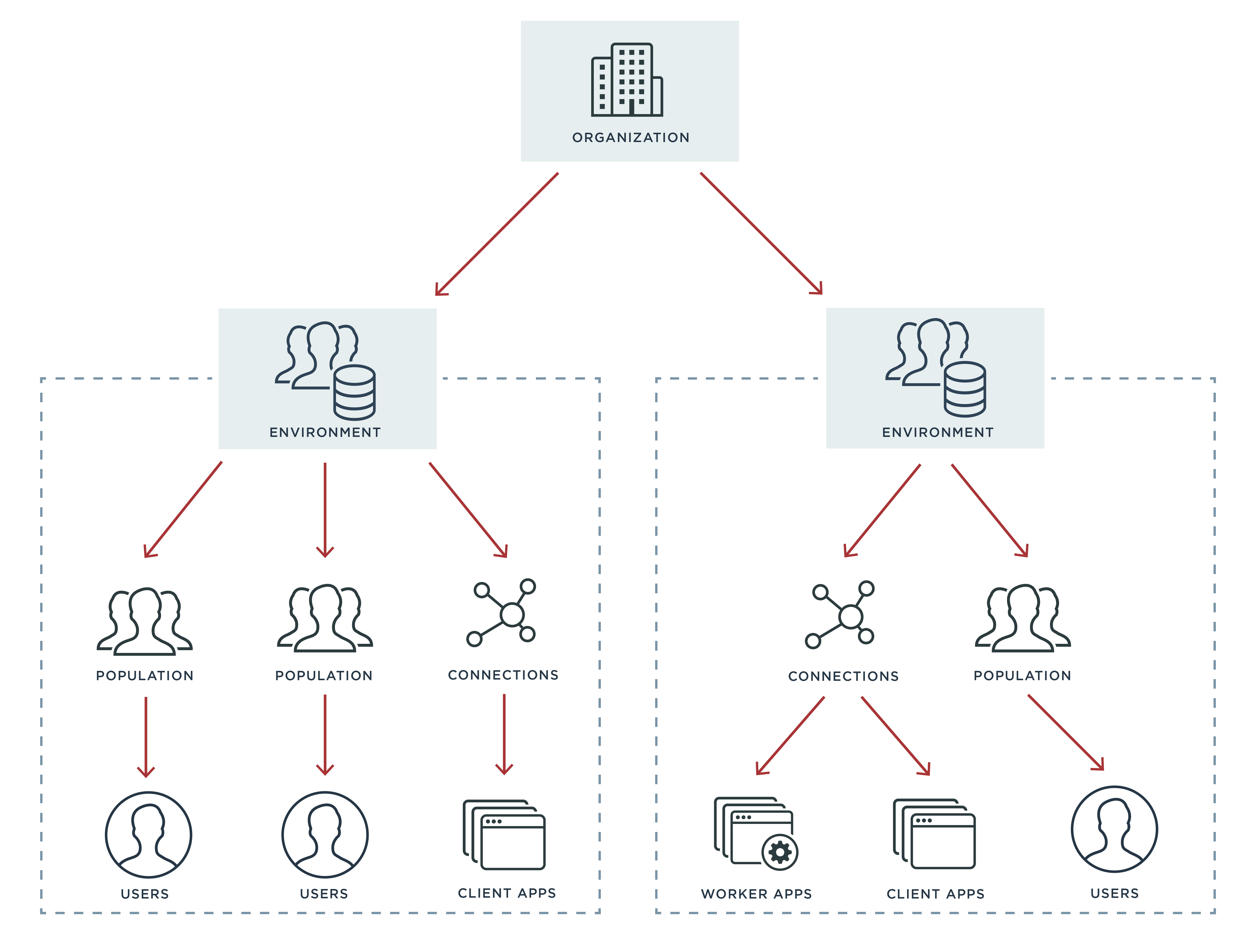
Here at Ping, we like to talk about how multitenancy within PingOne for Customers is a big benefit for our users. But why is that the case? What’s so great about multi-tenant solutions? First of all, multitenancy helps keep down the management costs associated with the solution. It allows Ping to be more efficient with the hardware resources we’re using to provide the service, and provide a better product to our customers.
The reason for this is because multiple tenants or environments that share a single resource can make more efficient use of that resource. For example, if your four separate environments each have their own resource, they each may only use a portion of their resource most of the time—say, for argument’s sake, 20%. That leaves a lot unused that you’re still paying for. If instead, we put those four environments on one cloud resource, together they take up 80%, and there’s still room for activity spikes. Now we’re only managing one hardware resource and you benefit from our efficiency. This oversimplifies things, but you get the idea.
Moving to a cloud solution that supports multitenancy also makes it easier to scale as demand requires. If there are separate resources to support each environment, there’ll probably be more management involved and more moving pieces. Management tasks might involve making decisions, configuring an entirely new resource or tearing a part out of a monolithic machine to change the size. With a shared resource, you just need to tack on something, whether that be storage, processors, memory or something else, to make it bigger, or remove a part to decrease the size. You’re virtually taking down and spinning smaller structures up within a larger structure, which is much easier on the overall system and significantly more cost efficient.
Multi-tenant solutions are particularly beneficial to those that need to combine certain benefits of having a shared resource with certain benefits of having separate environments. For example, you may need separate environments to allow you to follow region-specific data protection rules (like GDPR in the EU) in each one and prevent cross-contamination or accidental access.
In another case, you might have a situation in which you need an overview of all environments and centralized control, but still want to keep users partitioned into separate environments. Perhaps you have an admin in charge of the identity service as a whole, and she needs an overall view to help her decide when to provision new environments or adjust policies. Yet you have different engineering teams that should only have access to the environment(s) related to the product they’re working on. Again, multitenancy is the way to go, giving your admin the consolidated view she needs, while keeping environments and their users separated.