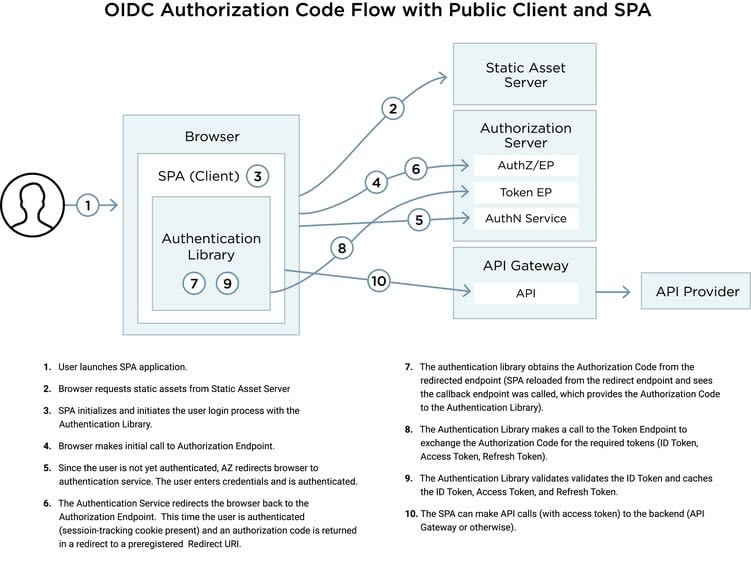
The traditional approach to using OAuth2 or OpenID Connect (OIDC) with Single Page Applications (SPAs) is the OAuth2 Implicit Grant or OIDC Implicit Flow, and many developers still use this approach. More recently, however, the use of the OAuth2 Authorization Code Grant (or OIDC Authorization Code Flow) with a Public Client has been on the rise. Identity Provider (IdP) vendors and bloggers have expressed varying opinions over using the OIDC Authorization Code Flow with a Public Client for SPAs, but this approach—with the proper safeguards—is viable and brings several benefits to the table, including:
- Use of refresh tokens. (This is a big one.)
- Greater control over the user session timeout via spec-defined mechanisms.
- Consistency across various use cases (SPA, native mobile apps, native desktop apps, web applications, etc).
I’ve explored these benefits in much greater detail in my previous blog posts. Going forward, the industry is moving toward using the OAuth2 Authorization Code Grant (or OIDC Authorization Code Flow) with a Public Client. In this blog post, we will explore how to best ensure this approach is used with SPAs in a secure manner.