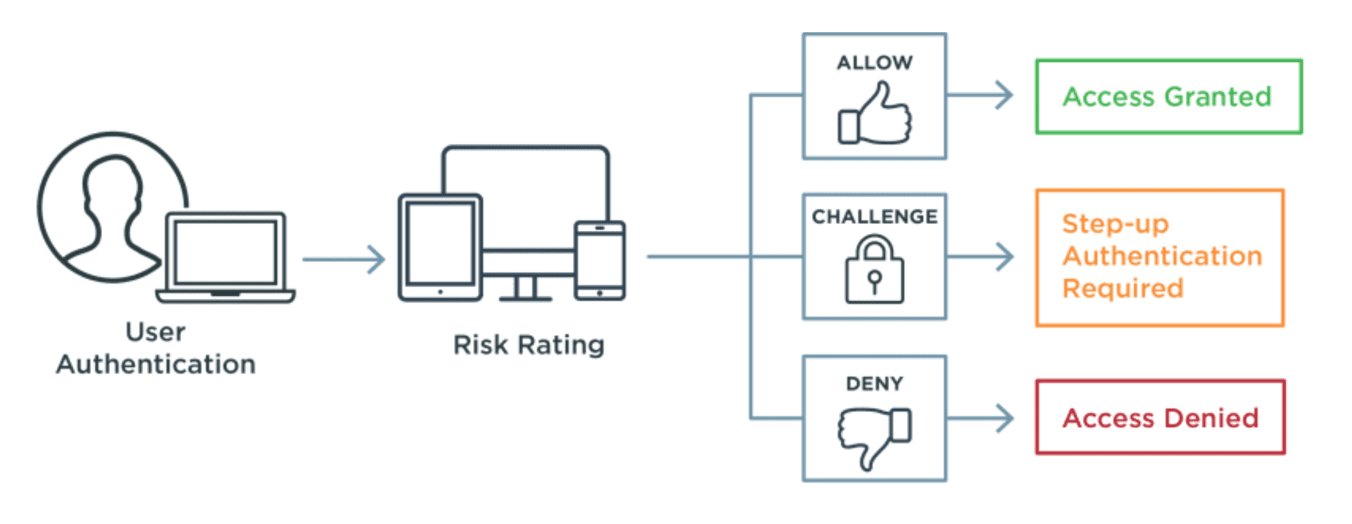
Privileged access management is a top cybersecurity priority for enterprises. According to Gartner, "nearly every successful security breach involves a failure of privileged access management (PAM)." While PAM isn't something we offer here at Ping, we recognize it as an important part of any security strategy and work with multiple partners to help put these critical controls into place. Read on to learn more about PAM and its importance.
Privileged access refers to the access or power granted to certain users above that of standard users to protect access to systems and sensitive data. Privileged access allows organizations to secure their infrastructure and applications, run business efficiently and maintain the confidentiality of sensitive data and critical infrastructure. Privileged access can be granted to human users or programmed applications. Types of privileged accounts include:
- Administrative accounts, including system, local and domain administrators
- Emergency accounts (also known as breakglass or firecall accounts)
- Service accounts
- Application accounts
- Domain service and directory accounts
Privileged accounts with the broadest abilities are known as superuser accounts. They have unrestricted capabilities, including the ability to implement system changes, access all files and directories, install software and delete data.