Strong Identity Governance can Protect Your Business and Increase Productivity
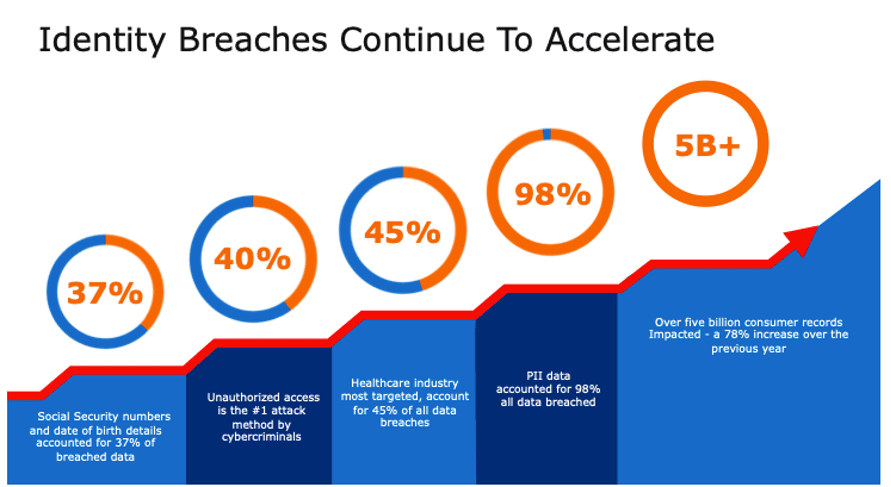
The risk of identity breaches to global organizations cannot be overstated. Cybercriminals continue to attack organizations across the enterprise and numerous verticals. As noted in the 2020 ForgeRock Consumer Identity Breach Report, unauthorized access (40%) is the number one attack method by cybercriminals in 2020. It’s no wonder there has been a 78% increase in compromised consumer records over the previous year. The point here is clear: organizations that are dependent on access predictions based on limited data and visibility are exposing their business to unnecessary risk. They need to evolve their current thinking and approach in order to better manage and control unauthorized user access.
The Silent Access Challenge: Entitlement Creep
Digital transformation, securing the remote workforce, and growing regulatory compliance requirements like SOX, HIPAA, GDPR, and CCPA are putting global organizations under increasing pressure to achieve compliance – not just annually, but continuously. With so many new types of identities – customers, partners, workforce, citizens, machines, devices, bots’ APIs, applications, and microservices – security and IT teams are overwhelmed. Today’s identity governance solutions cannot keep up because they are based on manual, human reviews and fulfillment. As a result, organizations are blind to potential risks such as growing employee entitlement creep across the enterprise.
An employee’s roles, groups, and responsibilities can change dramatically over the course of their employment. When these changes are dealt with manually, it is easy to forget to remove some or all access from a previous role. This leads to entitlement creep, where employees gradually accumulate unnecessary permissions over time. As a result, when a user leaves an organization, he or she might have more access than IT knows about, so the user retains access to those overlooked or orphaned accounts.
Organizational Blindspots Accelerate Entitlement Creep
Access Compliance
Staying compliant requires a lot of effort – especially when people change jobs, work on special projects, or leave your organization. Identity governance helps by automating the work it takes to enforce and demonstrate compliance. By implementing access policies, your organization can be confident that the right people are accessing the right information for the right reasons. And, it lets you quickly review and certify access for any user at any time.
Whether it is helping to comply with regulations such as SOX, HIPAA, GDPR, FISMA or CCPA, compliance is foundational to reducing your organization’s security risks. A failed compliance audit or lack of access controls can lead to users accumulating more entitlements or unnecessary permissions over time. This, in turn, can lead to inappropriate access privileges and potentially to larger issues as well, like unauthorized user access, or even a data breach.
Operational Inefficiencies
Identity governance solutions are meant to automate access requests, approvals, and certification reviews. Unfortunately, the reality is that IT and security teams are buried in access requests, approvals, and certification reviews. As a result, they can end up manually approving access requests and rubber-stamping access certifications. This results in the overprovisioning of user access privileges – in this case, excessive or unnecessary entitlement assignments. This can lead to unauthorized user access to systems, applications, and proprietary business information, like personal identifiable information (PII), business strategies, competitive intelligence or company revenue projections.
Business Enablement
Governing user access to applications and systems across an entire enterprise is a critical component to any security strategy. But it often presents one of the greatest challenges faced by security professionals. As employees, contractors, or temporary staff join the company, change jobs, take on different assignments, or eventually leave the company, organizations must constantly update access entitlements and policies to ensure that users only have access to what they need, while removing access they don’t.
Unfortunately, many organizations today address this with manual processes executed by different people and different systems. Manual processes are not effective at addressing the issue for a number of reasons:
1. Employees must wait to get the access they need to do their job.
2. They are more prone to errors.
3. Policies do not cover all needed access types and are often applied haphazardly.
4. They are much more costly than automated processes.
Eliminate Entitlement Creep with AI-Driven Identity Analytics
How do you prevent entitlement creep in your organization? The answer lies in artificial intelligence (AI)-driven identity analytics.
Identity analytics leverages AI and machine learning algorithms to consume and analyze vast data volumes to map out the user access landscape across the entire enterprise. By detecting user access patterns – both good and bad – identity analytics can quickly highlight excessive or unnecessary entitlement assignments and over-provisioned user access privileges. In turn, AI-driven identity analytics can automate the removal of high-confidence and low-risk access rights, lowering the risk of unauthorized users access across your organization.
In my next blog, I’ll explain how your organization can eliminate entitlement creep with ForgeRock Autonomous Identity. In the meantime, be sure to read the new KuppingerCole white paper “Overcoming Identity Governance Challenges with ForgeRock Autonomous Identity”.
You can view this post in Security Magazine.