You might be thinking: “But Dustin, that’s why we have an authorization standard called OAuth!” You’d be right for calling that out, since OAuth is the gold standard of authorization and the recommended way to do it. However, there are a few areas where OAuth falls a little short.
Decentralized Enforcement
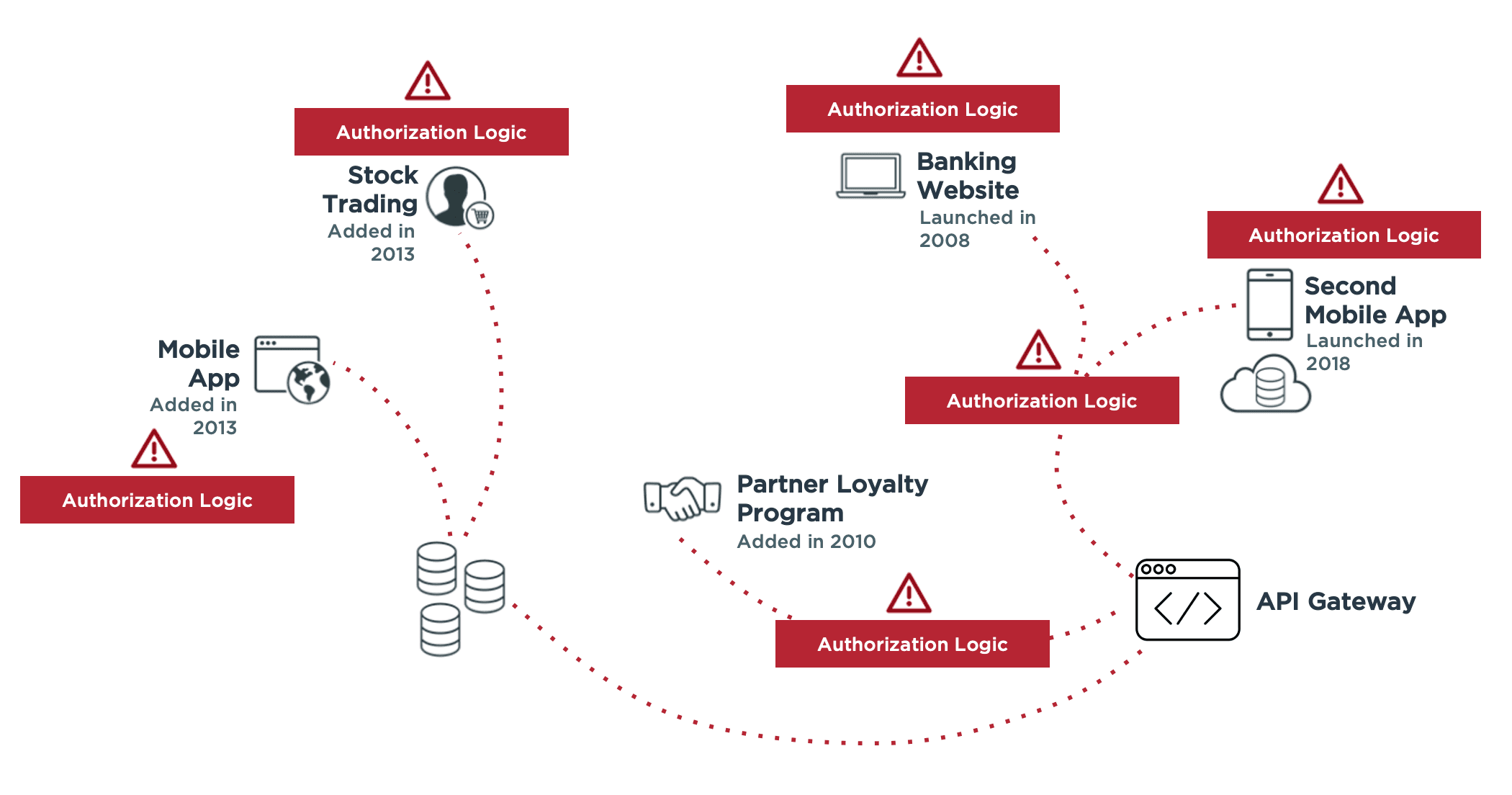
Gold standard or not, enforcement of access via OAuth is often implemented in various apps and layers of your infrastructure. As mentioned above, that can make it very difficult to audit or update. Imagine a situation where you need to change the authorization rules in a similar way across all applications, or a situation where you need to evaluate how access is granted to any app that has access to sensitive customer data. Pretty much any scenario that requires you to evaluate authorization beyond a single app will be difficult with OAuth alone.
Authorization and Data Access
OAuth generates tokens that are then passed to a resource (e.g., an application or a section of an application). If the token is valid, then access to that resource is granted. It does not help control access to data. For example, once access to a resource is granted, that resource or application may need to access data about a customer. Access to that data is not easily controlled by OAuth. Once access to the resource is granted, the resource’s access to data is out of scope—no pun intended.
Dynamic Authorization Scenarios
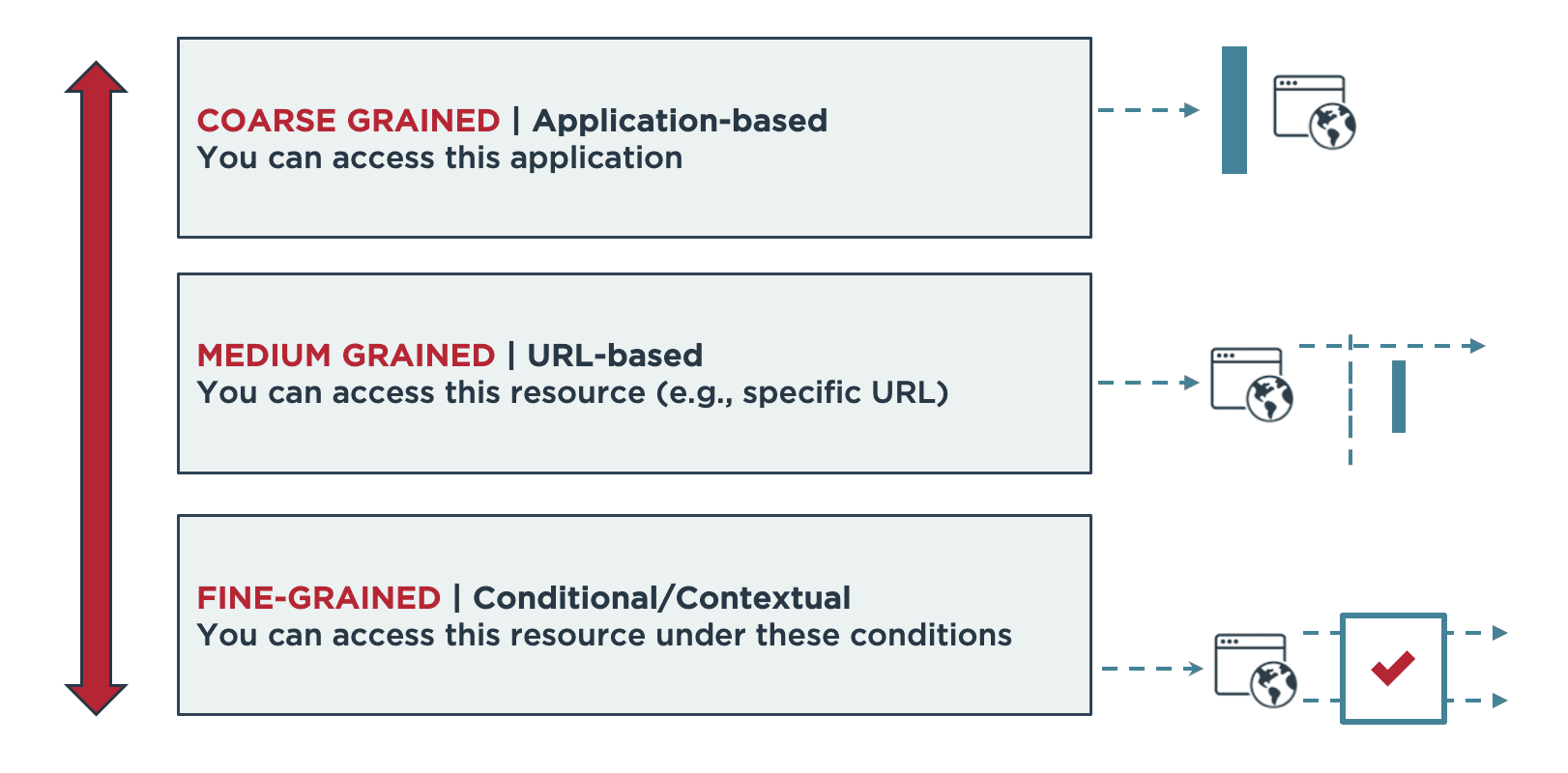
OAuth is great at controlling access to resources in static situations. If a certain type of user is always allowed to have access to certain types of resources, then OAuth works well. However, with more and more digital initiatives, we’re frequently seeing complex authorization scenarios that aren’t easy for OAuth to handle. The common thread in these scenarios is that the rules for authorization change depending on the situation. Take an example where customers are granted access to reports based on how many points they’ve purchased with a company. Just because a person is a “customer” doesn’t mean they should have access to a particular report, and the rules will change from customer to customer, depending on how many points they have. Consent enforcement also falls into this category. The consent a customer has given will vary from customer to customer and differ every time. We’ll dive into additional dynamic authorization use cases in the “Use Case” section below.
Predetermined Access
Another complexity that comes with dynamic authorization scenarios is that the authorization logic is often determined before it is enforced. The system that mints an OAuth token isn’t the same as the server that gives access to the resource. What if an attorney is authorized to access only 20 specific documents that pertain to their case out of millions of documents in the system? It is potentially inefficient to sift through the millions of potential documents and stuff authorizations to those 20 specific documents into a token. Practical limits to token data also can come into play. This situation can be problematic at scale with traditional authorization.
The good news is that there is a type of solution that can overcome these fundamental authorization issues and streamline authorization to ensure agility, security and compliance with new digital initiatives. They’re called “dynamic authorization” solutions.