I recently wrote a blog describing the OAuth 2.0 protocol using common characters in a way that’s a little more digestible than what you usually see. In researching OAuth 2.0, you’ll probably hear OpenID Connect a lot, and that it’s a protocol “built on top of OAuth.” Here, I’ll take the same friendly, digestible approach to OpenID Connect as I did with OAuth 2.0. (Check out my last OAuth Blog or this short video if you need an OAuth 2.0 refresher. Otherwise, let’s talk OpenID Connect.)
I know you might be thinking, “Another protocol? I thought we were secure with OAuth 2.0?” Well, OAuth 2.0 does a lot to add security to our apps and APIs, but its focus is on protecting the resource owner, or the end user, and their resources. OpenID Connect adds some extra assurance to protect the client.
OpenID Connect (OIDC) is a framework built on top of the OAuth 2.0 protocol to enhance its security, especially with identity management. OpenID Connect is your solution to verify who’s giving authorization to access the protected resource. In other words, OpenID Connect aims to add a way to more confidently answer the question, “Who gave authorization?”
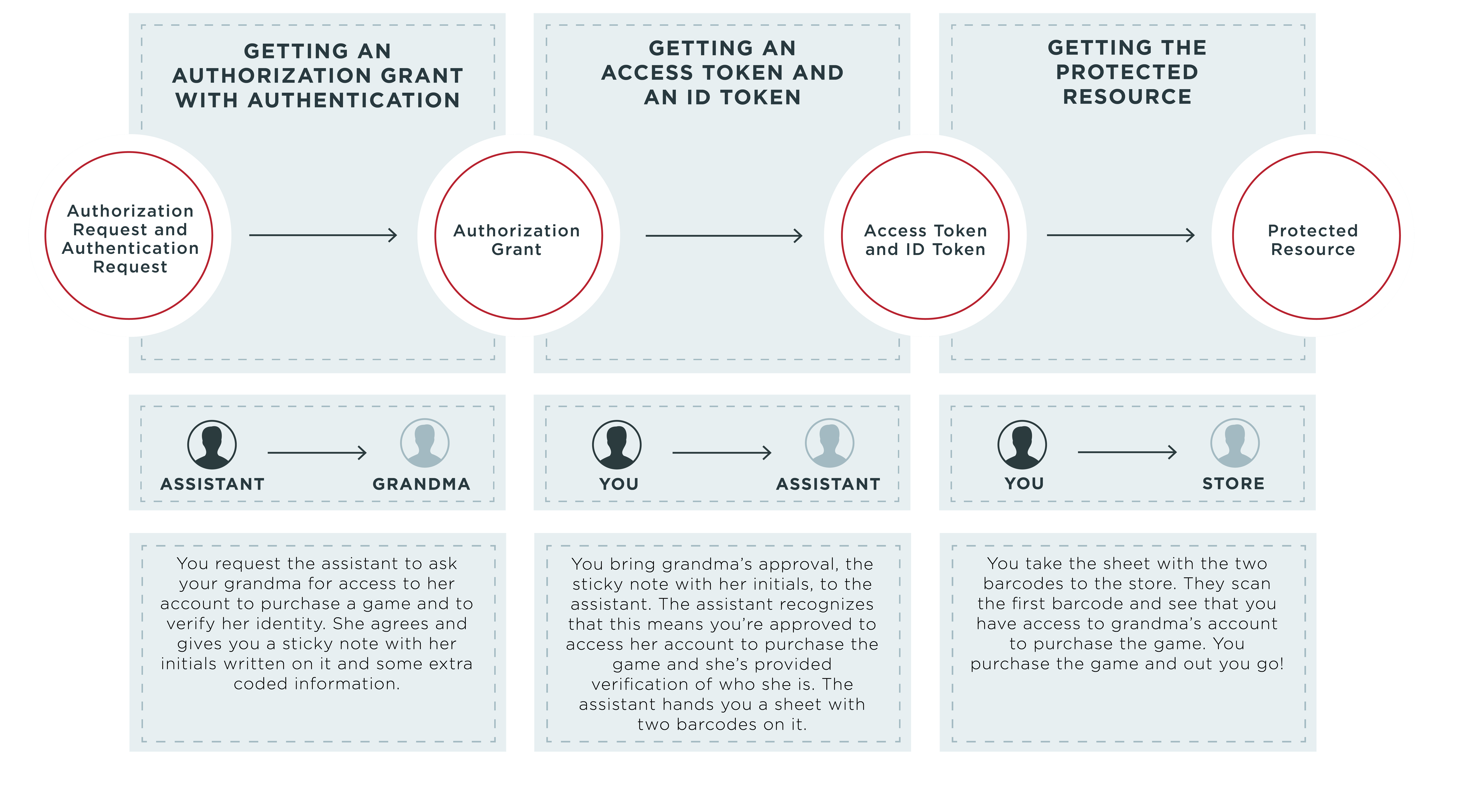
Unfortunately, resources explaining OpenID Connect also tend to make use of diagrams in the same style as OAuth 2.0 ones: a picture flooded with arrows back and forth, names, boxes and more that make it difficult to internalize what’s really going on at the core level. Using the story from my OAuth blog involving you, grandma and the video game store, we can come up with an analogy for the OpenID Connect protocol to make it easier to grasp the overall concept and reason behind creating it. We’ll break it down each step of the way and explain it in our analogy and in the terms the protocol uses to make it easy to compare to the OAuth 2.0 protocol and what issues it tries to fix.