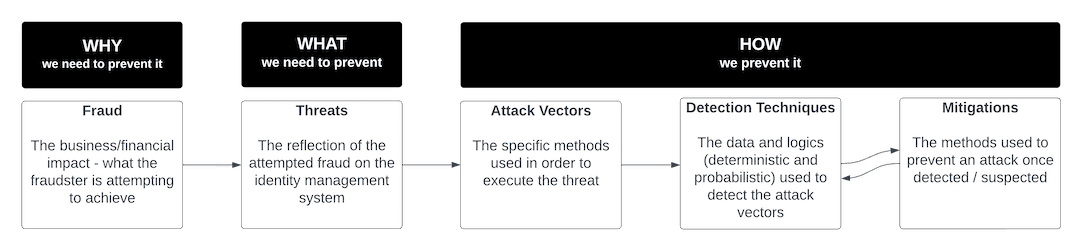
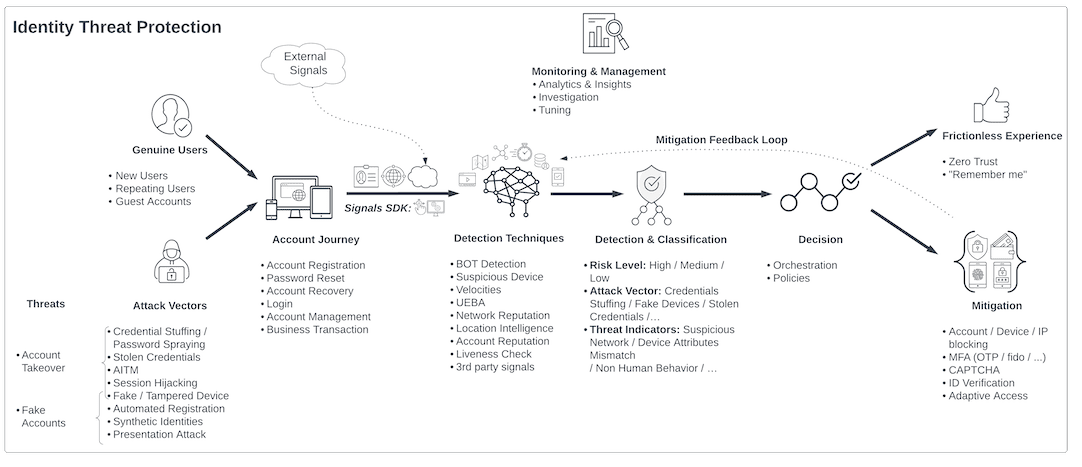
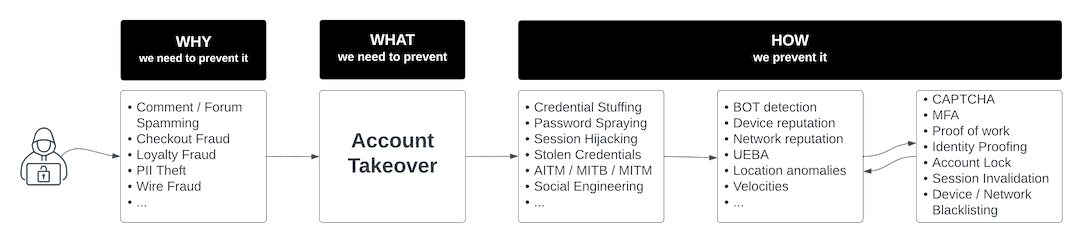
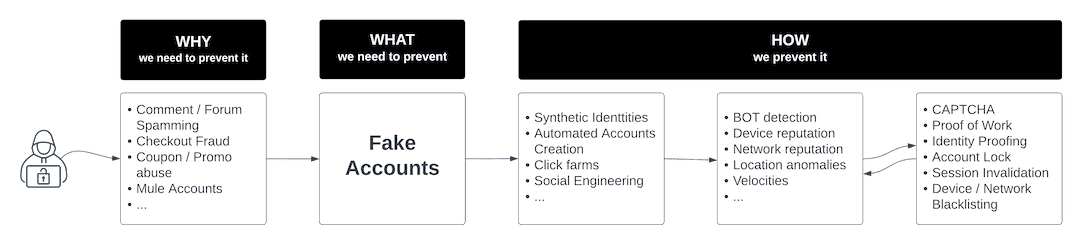
Now that you have a high-level view of your identity security posture, it's time to use the identity threat taxonomy to directly correlate specific threats with your own organization so you can develop actionable solutions for detection and mitigation.
Why Is the Attacker Interested in Your Organization?
By understanding what you have to lose, you also get a clearer picture of what a fraudster stands to gain by attacking your organization. To illustrate, if you operate an ecommerce platform that stores a good deal of user data, a fraudster may be after customer PII and credit card info. If you operate a bank, perhaps a fraudster is after your customers’ funds, or is looking to make a fraudulent application for credit in order to take your organization’s money directly. Regardless of your business type, knowing why criminals might be attracted to your organization lays the foundation for your threat prevention strategy.
What Types of Attacks Is Your Organization Most Vulnerable to?
The industry where you operate and the type of assets you are protecting directly impact the types of cyberattacks your organization might be vulnerable to. Similarly, your chosen security protocols like multi-factor authentication (MFA) also influence the type of attack a fraudster might choose to implement – for example, cybercriminals may deploy a sophisticated Adversary-in-the-Middle (AitM) phishing attack to get around MFA.
ATO is a common identity threat across all verticals because users often have many online accounts but use the same password across multiple platforms. Fraudsters may strike at an ecommerce site with an ATO in order to make fraudulent purchases with the payment method on file, or at a healthcare organization in order to harvest PII and PHI, or at a financial institution in order to make a transfer of funds. Conversely, NAF is much more common for businesses that offer loyalty programs and rewards points, or that offer new users direct access to funds. At Ping, we commonly see NAF challenges in financial services, where stolen or synthetic identity info is used to apply for lines of credit or loans, and in ecommerce and retail, where loyalty programs and sign-up bonuses are common.
How Will Your Organization Prevent These Specific Attacks?
Once you’ve mapped the specific attack vectors that your organization is vulnerable to, it's time to take action and find solutions with detection, mitigation, and prevention. While prevention is always a good strategy, detection and mitigation are critical pieces of the identity threat taxonomy structure.
Different types of mechanisms work to detect specific types of attacks. For example, bot detection is highly effective for credential stuffing attacks and for stopping large scale ATO campaigns. Other detection techniques look at things like device and IP info, or user location and behavior to assess whether a session is risky.
With your detection mechanisms operational, it's time to employ remediation strategies that offer challenges and changes to the user flow to stop specific types of attacks. For example, CAPTCHA is a relevant mitigation tool for stopping bots. However, CAPTCHA is useless when attempting to add friction for a user suspected of using stolen credentials to manually log in to an account. In this case, it may be more appropriate to call for MFA.