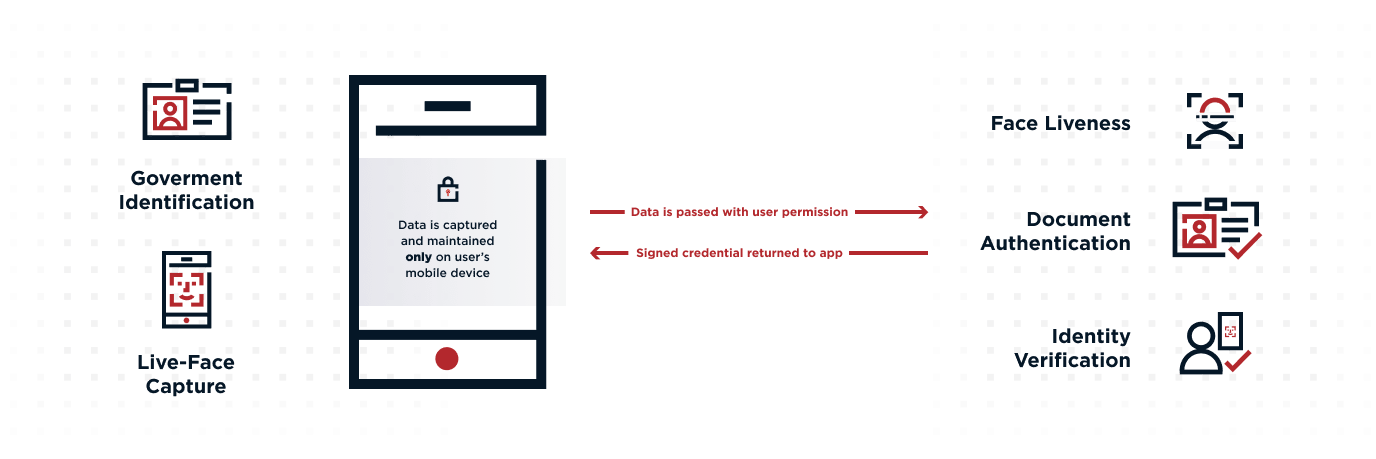
Identification, verification and authentication all have a role in identity management and security. Keeping bad actors from using stolen identities and credentials requires enterprises to be proactive. According to the FBI, internet crime costs Americans $4.2 billion in 2020.
Choosing the appropriate level of security depends on the application. For example, a financial services company with high-value assets and transactions typically requires more proof of identity than a social media company. Of course, that doesn't mean social media companies can forgo strong identity security measures. In 2016, hackers took over Katy Perry's Twitter account, which was the most followed account at the time.
Let's discuss how identification, verification and authentication are used for online identity management and security.