The FBI's latest report on Internet crime reveals an alarming increase in phishing, ransomware and malware attacks on U.S. companies. The FBI's Internet Crime Complaint Center (IC3) received nearly 20,000 reports last year of business email compromise/email account compromise (BEC/EAC) events—hackers compromising organization email accounts using intrusion and/or social engineering techniques—that caused companies to suffer almost $2 billion in losses. And the number of total complaints the IC3 receives has skyrocketed, up from roughly 300,000 complaints in 2016 to 790,000 in 2020.
Preventing hackers from infiltrating a company and jeopardizing its integrity is a full-time job for today's IT departments. Cybercriminals have access to a limitless amount of knowledge, tools and technology via the Dark Web. The sophistication and speed with which they use to compromise organizations continues to grow rapidly, with no end in sight.
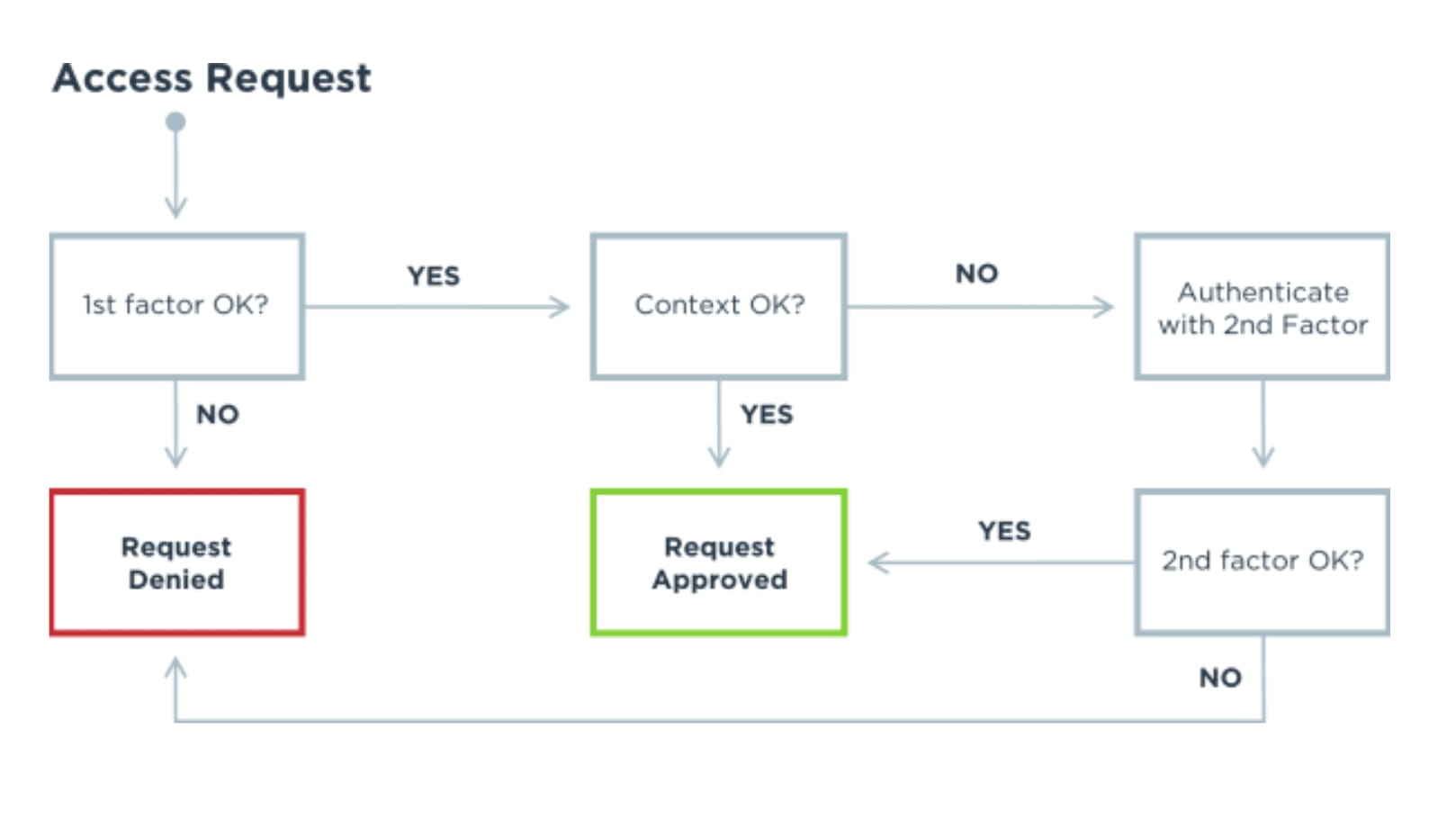
One of the most important tools for fighting cyberattacks is identity and access management, which ensures only the right people are accessing company resources. By providing authorized users with secure, seamless access to all their applications and resources from anywhere, companies unlock value while delivering better security.