Inappropriate Access Leads to Data Breaches
Inappropriate levels of access granted to employees, contractors, and partners is the leading cause of data loss, theft, and breaches. The number of external attacks has grown significantly in the last few years, and the sophistication of those threats has increased exponentially. The primary reason is cybercriminals’ use of new and emerging technologies, such as artificial intelligence (AI) and machine learning (ML).
Global organizations are being overrun by a flood of malware, phishing, and ransomware attacks and compromised credentials. A major factor: increasing coordination among hacker groups and state actors. The stats tell the story: "Breaches containing compromised credentials (usernames and passwords) increased +450% in 2020 and ransomware attacks in 2021 have already surpassed last year including sharp spikes in key verticals, including government (917%), education (615%), healthcare (594%) and retail (264%) organizations."
Global organizations’ state of readiness in the face of all the high-profile breaches does not paint a positive picture. Nearly 80% of senior IT employees and security leaders believe their company’s lack sufficient protection against cyberattacks. Despite increased IT security investments made in 2020, organizations remain susceptible to unauthorized access in data breaches. In the 2021 ForgeRock Consumer Identity Breach Report, ”for the third consecutive year unauthorized access was the most common type of breach, accounting for 43% of breaches.”
In an effort to address growing data breaches and losses, many organizations have adopted a role-based access control (RBAC) model.
What Is RBAC?
Role-based access control (RBAC) is a model for determining appropriate access to applications, systems, infrastructure, and other corporate technology assets. An employee's role determines the permissions granted to them. RBAC gives each user the access rights to only the information they need to do their job or task at hand, and prevents users from accessing information not relevant to their job. This is known as the “least privilege” principle and ensures they cannot access sensitive information unless it is necessary and appropriate to their role in the organization.
Roles consist of several components, including authorization, responsibility, and job description. So, for example, when an employee changes jobs, their access permissions usually change. When they join a group, they gain the permissions granted to that group. If they leave that group, they lose their access.
RBAC is an important tool for global organizations to control access to their most confidential data and business-critical applications.
Why RBAC Is Critical
Global organizations are under siege from growing cyberthreats. RBAC provides a front-line defense for intellectual property (IP) and customer and employee personally identifiable information (PII), protecting it from breaches, compromised credentials, and insider threats. Customer PII is the most common and most expensive type of record lost or stolen in a data breach. The average data breach costs $180 per customer PII record.
With a modern RBAC model in place, organizations can start to implement a “trust nothing, verify everything” approach, also known as Zero Trust. This least-privilege model can help reduce the average cost of a data breach. The average data breach costs $5.04 million in an organization without a Zero Trust architecture in place. In contrast, the average data breach costs $3.38 million in an organization with a Zero Trust model: a 42% cost difference.
The key takeaway? With a proper RBAC implementation, global organizations can reduce costs and avoid the reputational damage and loss of customer trust associated with data loss, theft, and breaches.
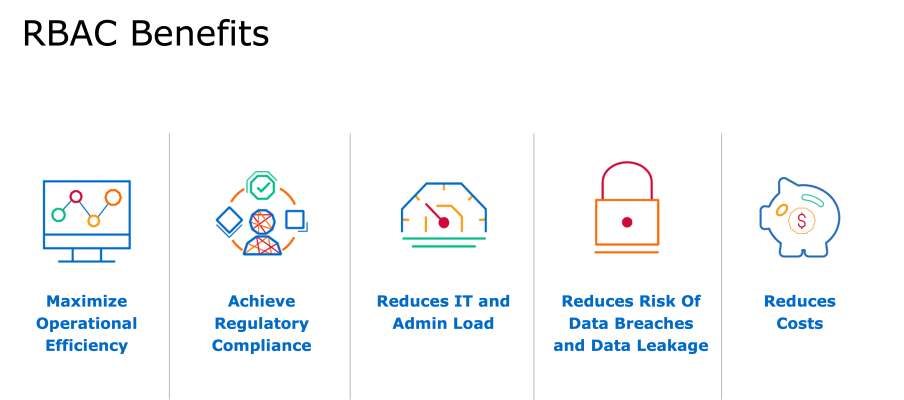
RBAC Benefits
Over the past decade, global organizations have leveraged RBAC to help them reduce administrative and IT support overhead, maximize operational efficiency, and improve regulatory compliance.
In addition to these macro-level benefits, RBAC provides organizational and employee advantages:
Organizational Benefits
- Reduced costs associated with user provisioning
- Improved system and application security
- Mitigation of “insider threat” attacks
- Better regulatory compliance and reporting
- Improved audit results and lower audit costs
- Increased employee productivity
Employee Benefits
- Simplified access request process
- Quicker access granted to systems and applications
- Faster annual or bi-annual access certification process
- Time-based access
- Smoother onboarding with quicker access to systems and applications
- Great user experiences
In my next blog, I’ll outline today’s RBAC dilemma, current business challenges, and ForgeRock’s approach to modernizing RBAC.
Want to learn more about how to modernize RBAC? Register for our webinar: A New Era: Maximize Zero Trust with AI-driven Role Management