In the first post of this three-part series, Harness the Power of Your Identity Data, we talked about the importance and potential power of using identity data to grow your business by providing tailored digital experiences. In our second post, we took a closer look at two of the three steps you can take to grow your business with identity data. The first step is to get connected to all of your various and siloed identity data sources. The second step is to leverage the built-in ForgeRock relationship model so that your data is arranged in a way that best supports your specific business needs. Read the details of steps one and two here. And now let's explore the third step.
Step 3: Scale Your Operations
Connecting your data silos and designing the desired relationships among different types of identity data lays a strong foundation for a converged identity and access management (IAM) platform. This concept can hold all of your identities in a single system while catering to the unique needs of different identity populations: customers, brands, partners, suppliers, employees, and devices. However, the benefits of bringing everything together under one roof can also introduce new complexity issues if you don't have a scalable way for your IT staff to manage ongoing operations and maintenance.
The identity management capabilities of the ForgeRock Identity Cloud include a feature known as the Organization Model, or Org Model for short. The Org Model is what helps you bring everything together to operationalize your identity data in a way that scales across your IT teams. The Org Model is an out-of-the-box identity object that has pre-defined relationships with other identity objects, such as users, roles, and applications. It empowers you to quickly create a hierarchy of "organizations," each with their own unique identity and attributes that support the tailored experiences you need to deliver for different populations of identities.
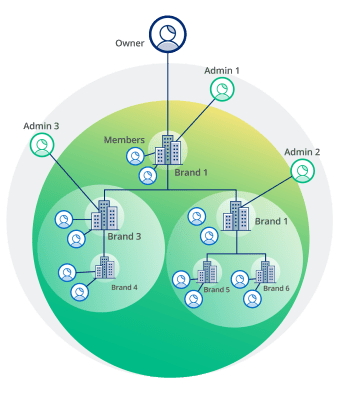
The easiest way to understand the Org Model is to imagine the organizational chart of any large company. Visualize interconnected boxes arranged in a top-down hierarchy. The CEO at the top maintains overall control and responsibility for the company, but also delegates specific responsibilities to leaders in finance, HR, legal, marketing, and other functional areas. Those leaders have specific autonomy to define the boxes in their organizations and the people within them. In the same way, our Org Model empowers you to define any kind of hierarchical identity structure that represents the reality of your business. And just like the company's organizational structure, our identity Org Model enables delegation so that the IT administrators that are closest to a given identity population can be put in charge of managing the organization, the users in it, and all the granular permissions and customizations required by that group of identities. This is the first half of how you scale your identity management operations.
With the ability to implement a scalable span of control through delegated administration, the Org Model is similar to how a company's organizational structure scales as it grows and changes over time. Let's look at one more analogy to understand the second half of scaling your identity management operations: inheritance.
Imagine an organization with many franchises around the country or even the world. Whether the franchise is a fast food chain, or an automotive dealership, certain policies and multi-brand experiences need to remain consistent. Other facets of the business need to be flexible to accommodate different supply chains, partners, and local government policies. This is why inheritance capabilities are so important. With the ForgeRock Org Model, changes made to the top-level organization, such as new access policies or authentication requirements, can automatically get pushed down to the sub-Orgs without requiring administrative intervention. And where required, separate organizational structures can maintain distinct policies, all subject to the requirements of the business.
Take the example of an automotive manufacturer looking to manage all of its independent dealerships and you giving them the flexibility to manage their business while maintaining a certain level of central visibility and control. The top CEO box in the manufacturer's Org Model gives the company this level of control in their world of digital identity. Next, the company creates Level 2 boxes, or "Orgs," for each of their defined regions in the U.S. This gives regional managers a level of control over the dealerships in their territory. The Level 2 boxes are connected and roll up to the Level 1 CEO box, just as in a company's organizational chart
At the third level, new Org boxes are created, which also have their own unique identity, relationships in the identity hierarchy, and the ability to have custom attributes. These Orgs are created to represent each dealership. And the owner of each dealership is given the authority (delegation) to manage certain aspects of the user experience. These could be different multifactor authentication (MFA) enrollment choices, for example. Then there's the inheritance factor, which dictates certain configuration consistencies across the entirety of the organization–maybe in this case a password length and complexity policy.
Using Identity Data to Drive the Runtime User Experience
Now that your identity data is organized according to your business needs and you have a scalable process for managing the maintenance and dynamic changes that are the reality of your business, it's time to put the data to work on the front lines.
This is where identity data meets access orchestration. With the right data at your disposal and an access management system with dynamic orchestration capabilities, each user's experience can be tailored to their specific needs. In one moment, a customer of yours enters their account name and, based on the data retrieved and fed into the orchestration workflow, this customer experiences a low-friction, passwordless login that is personalized. At the very same moment, one of your suppliers enters their account name into a different application and receives a tailored MFA experience based on the security negotiated between your company and the supplier's company. For this supplier, union rules prevent management from requiring their users to authenticate on their personal mobile phones. So based on your identity data, including this supplier's Org Model affiliation, the user receives a sign-in link by email. When the user clicks on the link from the computer, the user signs in with a passwordless experience that doesn't require the use of a phone.
To learn more about how you can grow your business with identity data, check out the replay of our recent webinar with Forrester, titled "How to Deliver Tailored Multi-Brand Experiences from a Single Identity Platform."