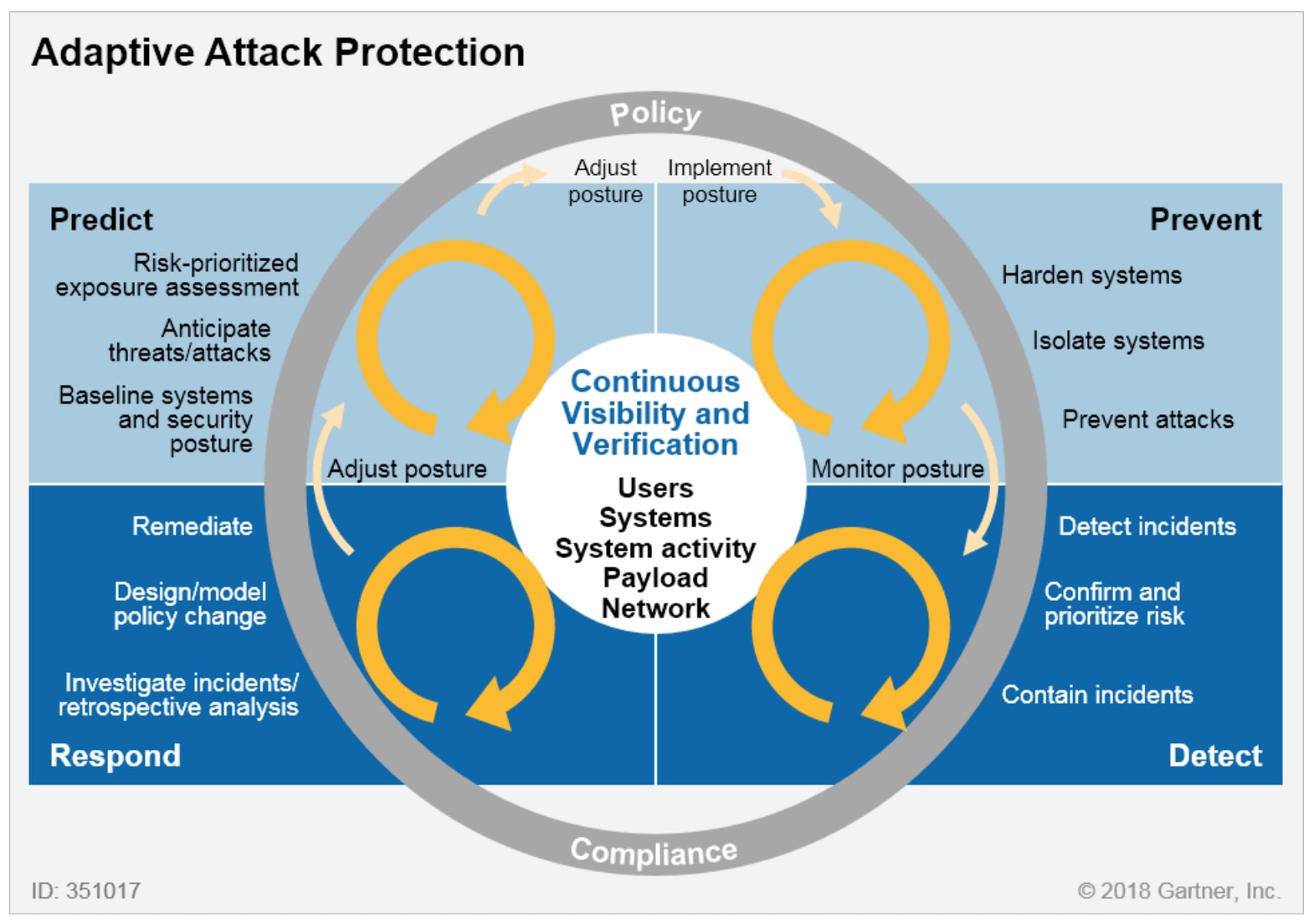
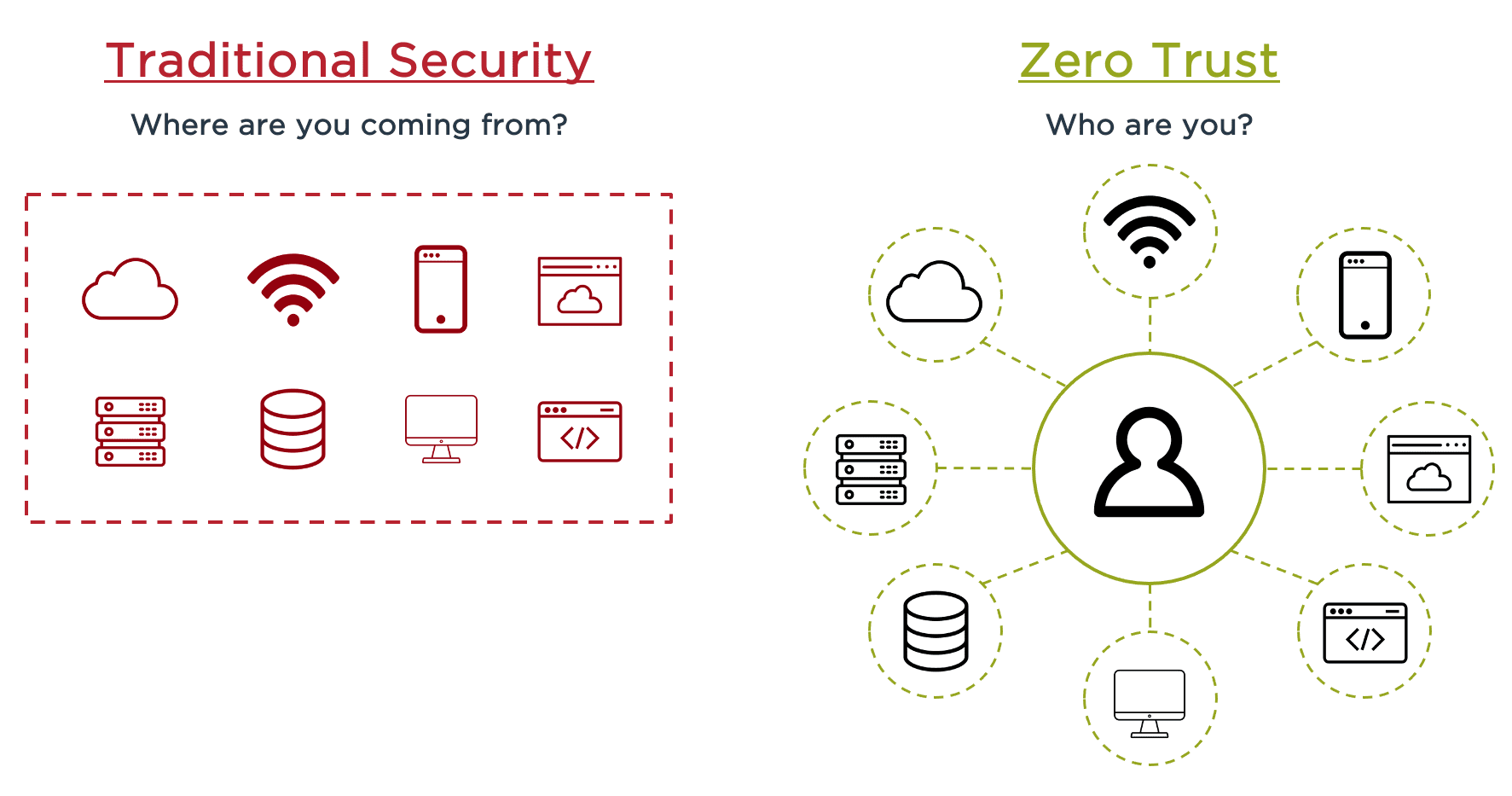
The Zero Trust party is in full swing. The security concept had been around long before COVID-19 as the way forward in managing the increasing number of resources outside of the corporate network like mobile devices, IoT, cloud computing and small instances of remote work. But while many organizations had been experimenting with Zero Trust, they still relied on the perimeter-based approach—until the global pandemic changed everything.
Almost overnight, Zero Trust went from a nice-to-have to a necessity as companies shifted entire workforces to a remote work environment. In our recent survey of 1,300 executives worldwide:
82% have already adopted some type of Zero Trust element
71% say their Zero Trust investments will increase in the next 12 months
85% believe identity security technologies are critical to mobile and/or user experience
Clearly, executives see the value, but each organization will deploy Zero Trust in different ways. Prior infrastructure investments, varying levels of cybersecurity knowledge and executive buy-in can influence how (and how quickly) a company adopts a Zero Trust architecture. So how do you determine the best approach for your enterprise to get started with Zero Trust?