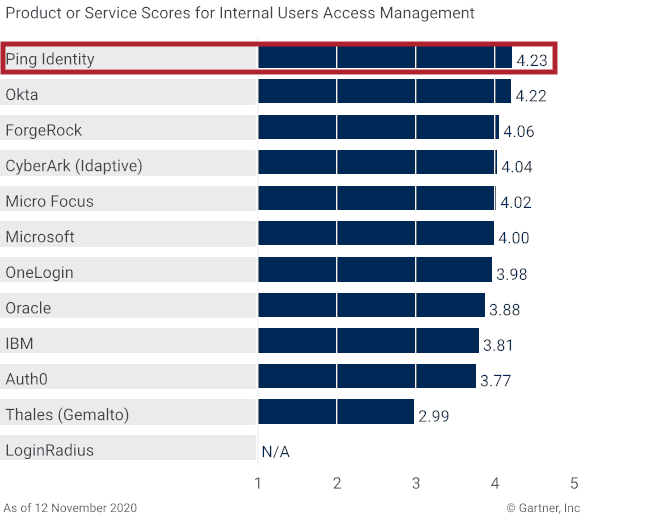
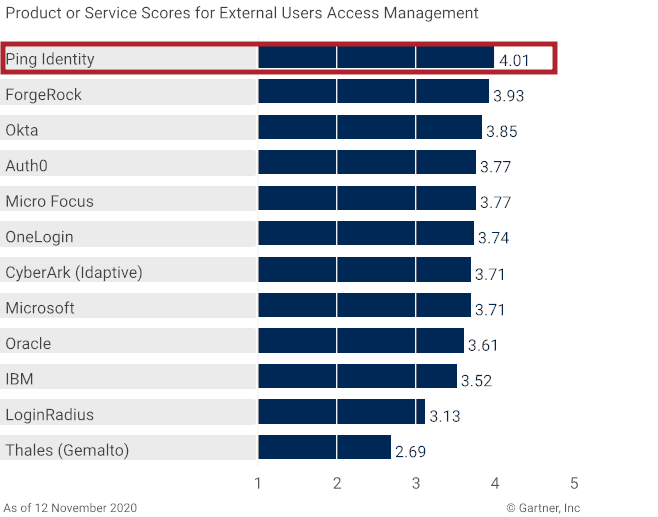
The biggest takeaway from Gartner’s Magic Quadrant and Critical Capabilities reports: modern, highly capable access management tools have never been more critical for organizations' digital transformation initiatives. Gartner attributes this critical need to a few factors.
The Sudden Shift to Remote Work
The trend toward a mobile, distributed workforce, including working from home, has been underway for many years. Unfortunately, sudden events like COVID-19 can shine a harsh spotlight on the need to provide a more comprehensive workforce access and productivity solution than many companies have in place currently.
Gartner is seeing the market increasingly embracing this long term. According to their Forecast Analysis, “through 2024, approximately 30% of all employees working remotely will permanently work from home. By the end of 2024, the change in the nature of work will increase the total available remote worker market to 60% of all employees...By 2024, in-person meetings will drop from 60% of enterprise meetings to 25%, driven by remote work and changing workforce demographics.”1
Working from home is no longer just a perk to offer employees, but an essential alternative to keep your business running. Ping is prepared to help IT organizations ensure employees can be secure and productive anywhere in the world.
Acceleration of Digital Customer Experience Initiatives
The world events also accelerated the move to digital business and caused an immediate demand for online access. This surfaced weaknesses for many companies who needed to provide a fully digital experience and placed a premium on those that were providing one.
Customers want two simple things as they interact with brands. First, they want brands to delight them by providing great user experiences. Second, they want brands to protect them from fraud, breaches and privacy violations. CIAM helps you do both.
Delighting your customers means ensuring their journey—from their initial introduction to your brand to the time they become your loyal advocates—is as smooth as possible. If you fall short of providing an exceptional experience, your customers may go elsewhere. Given what’s at stake, a great customer experience is no longer just nice to have; it's a critical differentiator.
You can’t stop at experience either. Customers also care deeply about security. A 2019 Ping Identity report revealed that 81% of customers would stop engaging with a brand online following a breach (a 3% increase over 2018), and one in four would stop all interaction whatsoever. The most recent Cost of a Data Breach study found that of the $3.92 million average cost of a data breach, 36% of the total, or $1.42 million, was the direct result of lost business.
Adoption of Zero Trust Security Models
Enterprises are accelerating digital transformation initiatives in response to the rapidly evolving business landscape. Successfully implementing business-critical digital transformation efforts requires an efficient, effective workforce that has access to every application and tool they need to get their job done.
However, security leaders are faced with the difficult challenge of balancing the security of their organizations with keeping employees productive by providing access to resources from anywhere, at any time. Maintaining this balance requires an organization to have full confidence in the identity of the employee requesting access to ensure only the right users gain access to the resources they’re authorized to use.
In response, organizations are adopting Zero Trust. Zero Trust is a strategic concept that encourages security teams to rely less on the safety of a network perimeter and more on the identity of the user and the secure processes and technologies that can be applied directly to corporate resources, irrespective of where they’re located. Gartner takes this a step further by applying seven imperatives of a continuous adaptive risk and trust assessment, or CARTA. According to Gartner research, “While zero trust is the initial security posture, CARTA envisions enterprise security infrastructure as continuously adaptive based on real-time assessments of risk/trust throughout the life cycle of a user’s access.”2
Ping further addressed the need for Zero Trust and CARTA approaches this year with PingOne Protect, a cloud service that uses machine learning to evaluate risk signals and detect threats in real time. It evaluates multiple signals to understand the level of risk posed by a user attempting to access a particular resource, including UEBA, anonymous network detection, impossible travel detection and the reputation of a user’s IP address.
Make the Best IAM Decisions for Your Needs
There are many trends and capabilities to consider, but you don’t need to go it alone. We’re pleased to provide access to the 2020 Gartner Magic Quadrant for Access Management to help you evaluate solutions against your unique objectives and requirements. Download your complimentary copy of the report.
SOURCES:
1Ranjit Anwal, Anna Griffen, Rishi Padhi, and Namrata Banerjee, “Forecast Analysis: Remote Workers Forecast, Worldwide,” Gartner, August 2020.
2Michael Kelley, Abhyuday Data, and Henrique Teixeira, “Secure Application Access by Applying the Imperatives of CARTA to Access Management,” Gartner, February 2020.