As feedback has been shared on the first blog about the Department of Defense Zero Trust Strategy, the primary responses were:
"OK, how does ForgeRock do what you've claimed?"
"Is that all ForgeRock does to meet the user pillar of the Zero Trust architecture?"
Constructive feedback is always appreciated. The feedback provided structure for a response. In this blog, we are focusing on the user pillar in the Zero Trust Architecture. It contains the requirements for proofing, authentication, authorization and governance of identities and Non-Person Entities (NPE).
In the Department of Defense Zero Trust Architecture (ZTA), there are five major tenets that influence all aspects of Zero Trust. They are:
- Assume a hostile environment
- Presume breach
- Never trust, always verify
- Scrutinize explicitly
- Apply unified analytics
These guidelines offer a straightforward approach to assess whether a proposed solution is suitable for a given pillar under the ZTA framework.
For the user pillar, the processes executed for the continuous authentication, continuous authorization, and User Event Behavior Analytics (UEBA) are key to meeting the tenets of the ZTA. ForgeRock meets these Zero Trust requirements by providing features in three main categories. They are:
- Identity orchestration for user journeys
- Partner integrations
- Flexible deployment model
Identity Orchestration for User Journeys
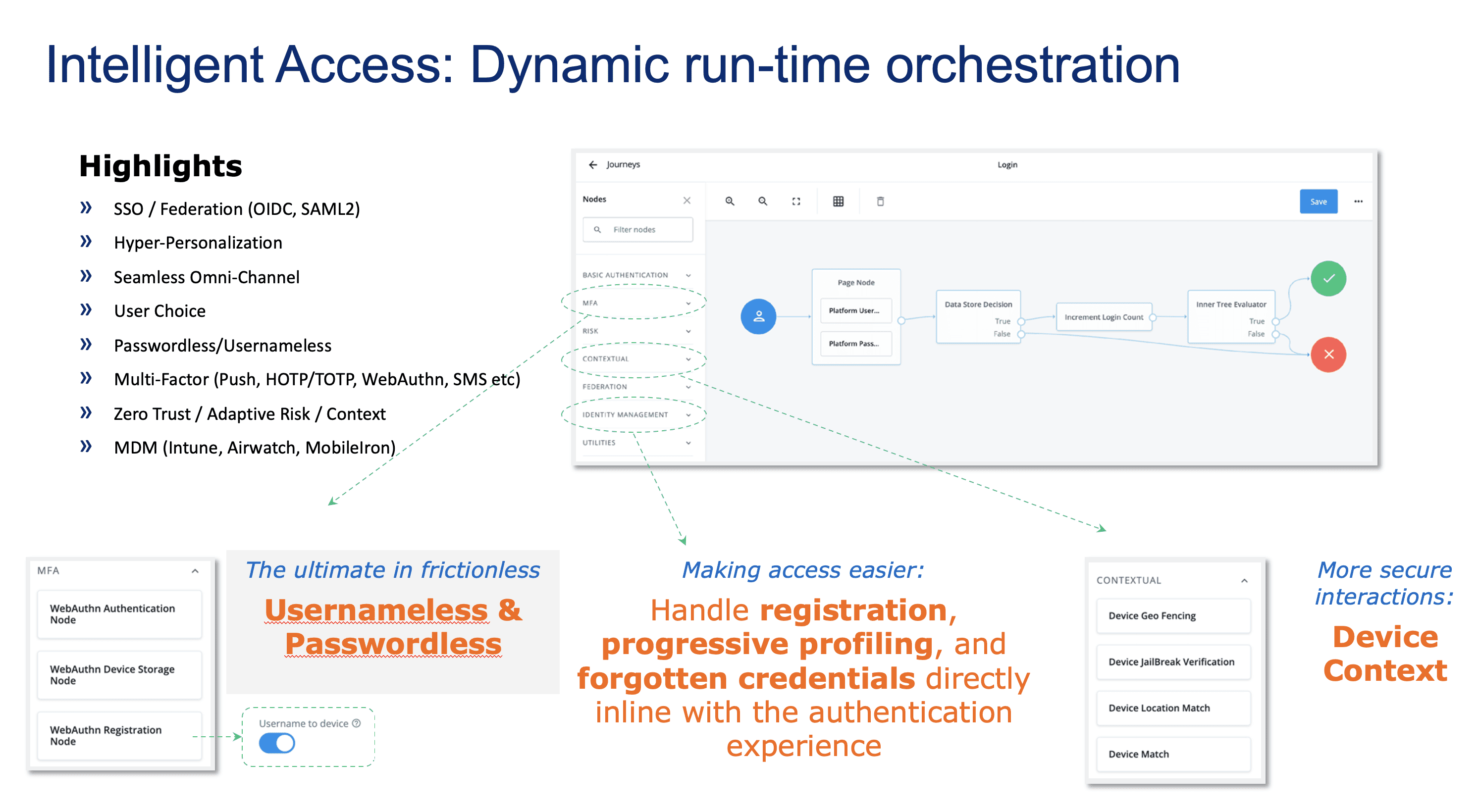
Journeys enable dynamic run-time identity orchestration for processes ranging from the highlights referenced in the image below:
The journey builder allows for changes to be made and tested in a real-time environment. With over 100 pre-built nodes to use in your journeys, processes that used to require scripting are now accomplished through simple drag-and-drop actions.
The robust flexibility created by the ForgeRock identity orchestration engine lets you design processes that enforce the tenets of ZTA, as listed above. Since the circumstances, mission requirements, and attack plane are different for every group in DoD, it is vital for there to be choices that still meet the tenets but also provide flexibility for different scenarios.
Partner Integrations
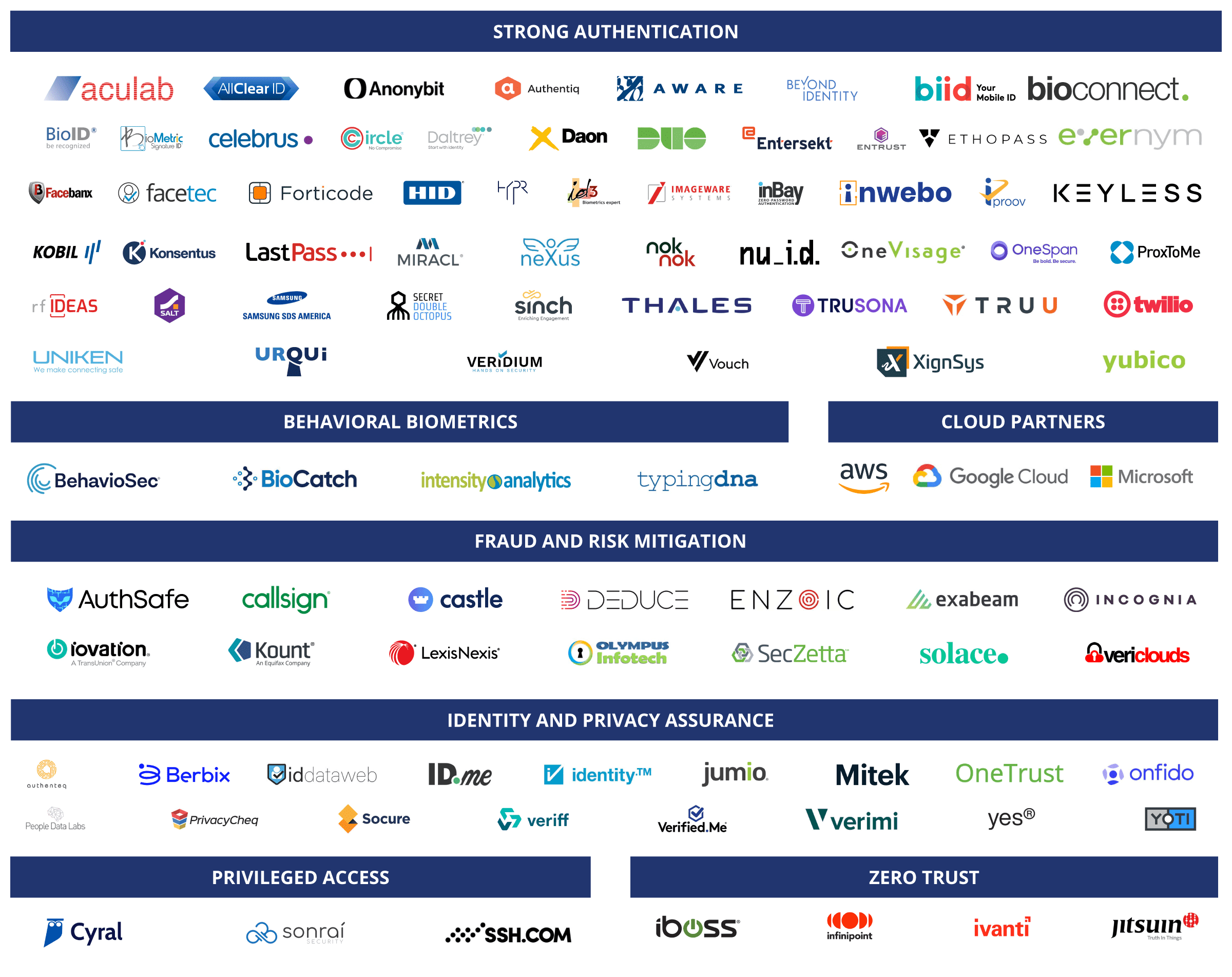
ForgeRock has built a large network of technology partners that have proven integrations with ForgeRock technology.
The ForgeRock Trust Network is a robust, growing network that enables ForgeRock customers to leverage solutions that improve the strength of their ZTA user experience and security. ForgeRock is always seeking new technology partners. This network will grow organically as new solutions come to market leveraging new technology innovations.
Flexible Deployment Model
ForgeRock's deployments in the Department of Defense, from small to large mission groups, is a natural result of our flexible deployment model. ForgeRock is compliant with Defense Information Systems Agency Security Technical Implementation Guides (DISA STIG) and has deployments at every Impact Level. It is common for ForgeRock to be deployed in Denied, Disrupted, Interrupted, and Limited (DDIL) and low-bandwidth environments. The different deployments can synchronize with a main instance of ForgeRock located in a centralized deployment in the cloud or in a mission-specific data center. ForgeRock supports a central user repository and a base set of configurations, enforced at the mission or branch level, while still providing the ability for varied deployments to be configured differently based on mission requirements.
Reducing Risk
ForgeRock's robust identity orchestration engine, mature technology partner network, and flexible deployment model facilitate your ability to meet mission requirements in the user pillar of the ZTA framework. Risks change frequently, requiring a change in approach, one of the main requirements of a working Zero Trust Architecture.
When considering an identity vendor to partner with you in your ZTA journey, these three criteria are essential. Without any one of the three, you will find areas where you cannot meet the ZTA requirements and tenets.
In part 3 of this blog series, we will discuss the details of each tenet and how ForgeRock meets that tenet in the user pillar of the Zero Trust Architecture.
Learn more about how ForgeRock delivers Zero Trust for the Department of Defense here.