On November 7, 2022, the United States Department of Defense (DoD) released a new Zero Trust strategy, clarifying the goals and timeline for modernizing the Department's defense strategy.
In the forward, the report says, "We all must play a role in combating our adversaries by acting quickly and correctly to address security threats wherever and whenever they arise." The report notes that the changes necessary to transform DoD IT resources from a "castle-and-moat" model to a Zero Trust model will require a coordinated, full-department effort. The forward continues, "If we do not do this together, our teammates' vulnerabilities will remain exposed and open to attack, which makes all of us less strong." This statement affirms that global information warfare is an increasing challenge for our service members, compromising mission safety and outcomes.
"We all must play a role in combating our adversaries by acting quickly and correctly to address security threats wherever and whenever they arise."
– DoD Zero Trust Strategy, October 21, 2022
The strategy promotes a fully implemented Zero Trust framework that "...will reduce the attack surface, reduce risk, offer opportunities to manage the full range of risks…and enable more effective data-sharing in partnership environments." This new strategy affects all users, Non-classified Internet Protocol Router Network (NIPRNet) and Secret Internet Protocol Router Network (SIPRNet) networks, and IT infrastructure in the DoD. The DoD has identified an aggressive schedule to get a fully functional framework implemented by the end of FY 2027. This is a monumental task considering the number of users and IT infrastructure that will be impacted, including the legacy systems that will likely need modernization.
Hastened by the need to support a remote workforce and an increase in international partnerships, the DoD is reevaluating its approach to securing intellectual property.
There is a department-wide initiative to migrate to cloud-supported software solutions (SaaS) that can meet DoD requirements. At the same time, the Department must support warfighters in low-bandwidth, Denied, Disrupted, Interrupted, and Limited (DDIL) mission scenarios, requiring some of the Zero Trust solutions to run on local infrastructure, which eliminates the effectiveness of SaaS solutions.
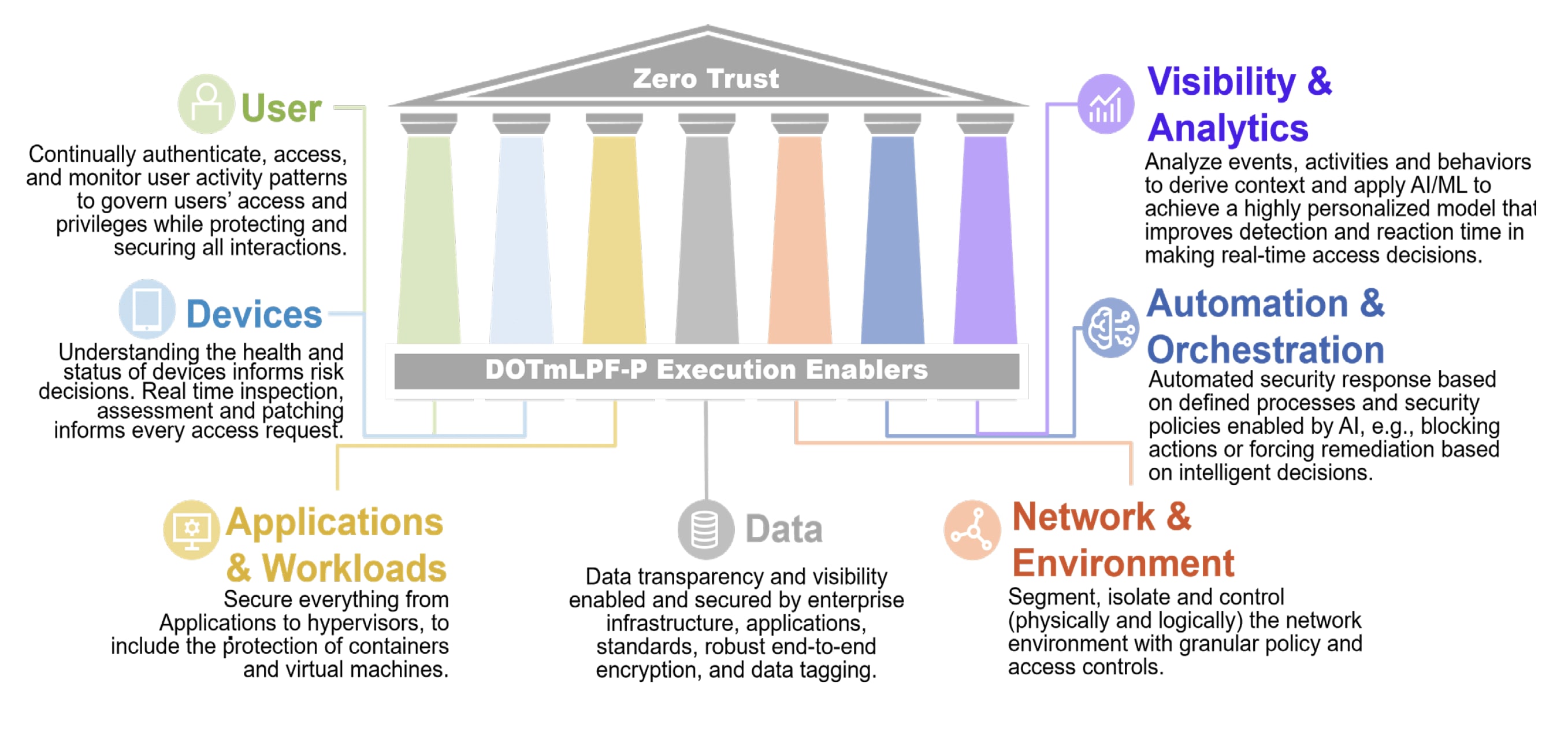
DoD Pillars of Zero Trust (source: DoD Zero Trust Strategy report)
Software deployment flexibility is essential for the DoD to meet the unique requirements identified for the DoD Zero Trust Strategy. ForgeRock offers a flexible deployment model by offering feature parity between its deployment offerings: the ForgeRock Identity Cloud SaaS solution, a fully DevOps- enabled deployment, and a traditional software deployment. ForgeRock is currently working in many different mission areas within DoD, from running in the cloud to being deployed in DDIL environments. ForgeRock's deployment models allow our solutions to be deployed in environments from Impact Level (IL) 2 to IL 6.
ForgeRock is a fully featured identity and access management platform that will provide the DoD with deployment choices that meet the full array of use cases in the User pillar of the DoD Zero Trust Strategy. Also included in the platform is user journey orchestration that incorporates knowledge of the users' Devices – looking for signs that the device is registered to the user and checking if a device is jailbroken/rooted. The platform is infused with artificial intelligence (AI)-powered Visibility and Analytics to monitor login requests in real-time, block malicious attempts, and require step-up authentication when anomalous behaviors are detected.
ForgeRock follows emerging and evolving identity standards closely to quickly implement the software changes required to meet their specifications. Our focus is on allowing our customers to have the latest Zero Trust identity features, including those that cover authorization, authentication, lifecycle management, and governance.
For further information on how ForgeRock can help the DoD meet the new Zero Trust strategy, please follow this link.


