Ping’s solutions for government are now DOD Impact Level 5 (IL5) certified. For defense organizations of all kinds, this means ICAM modernization for National Security Systems (NSSs) and Controlled Unclassified Information (CUI) is now attainable.
DOD IL5 and You: The Right Level of Controls for Your Defense Mission
What is DOD IL5?
The Defense Information Systems Agency (DISA), a combat support agency that provides IT support to the DOD, developed the Impact Level system as a way of identifying various information’s sensitivity, who should have access to it, and what controls should be in place to protect it.
DISA’s Cloud Computing Security Requirements Guide (CC SRG) offers a security model and guidelines for the necessary controls for defense agencies, suppliers, and contractors to securely utilize cloud computing. The DOD releases SRGs for various different technology groups, and the cloud computing one is specifically stringent: running defense applications on a cloud infrastructure has runtime availability, secure access, and cost implications that must be considered.
What Kind of Information Does DOD IL5 Protect?
DOD IL5 is a cybersecurity term to classify the level of security controls and protection required for sensitive information and mission-critical systems in cloud environments. The DOD CC SRG defines IL5 as the highest level of security controls required for unclassified data (CUI) that is deemed mission-critical, including data that could potentially result in the loss of life, catastrophic damage to national security, or grave damage to the DOD's ability to conduct its operations.
Due to the severe consequences around loss of data designated for IL5 compliance, the security controls required for IL5 are extremely stringent and include measures such as continuous monitoring, advanced access controls, data encryption, and other security protocols to ensure that the data is protected from unauthorized access, manipulation, or theft.
What’s the Difference Between DOD IL5 and FedRAMP?
While both the Federal Risk and Authorization Management Program (FedRAMP) and the DOD Impact Levels are focused on security controls for cloud products and services, their scope and focus are different.
FedRAMP is a government-wide program and focuses on ensuring the security and privacy of cloud-based systems that store or process federal government data, including sensitive information such as Personally Identifiable Information (PII) and Protected Health Information (PHI).
The DoD Impact Levels, on the other hand, are DOD-specific cybersecurity standards meant to classify the level of security controls and protection required for sensitive information and mission-critical systems. Additionally, the DOD leverages FedRAMP’s assessment where applicable.
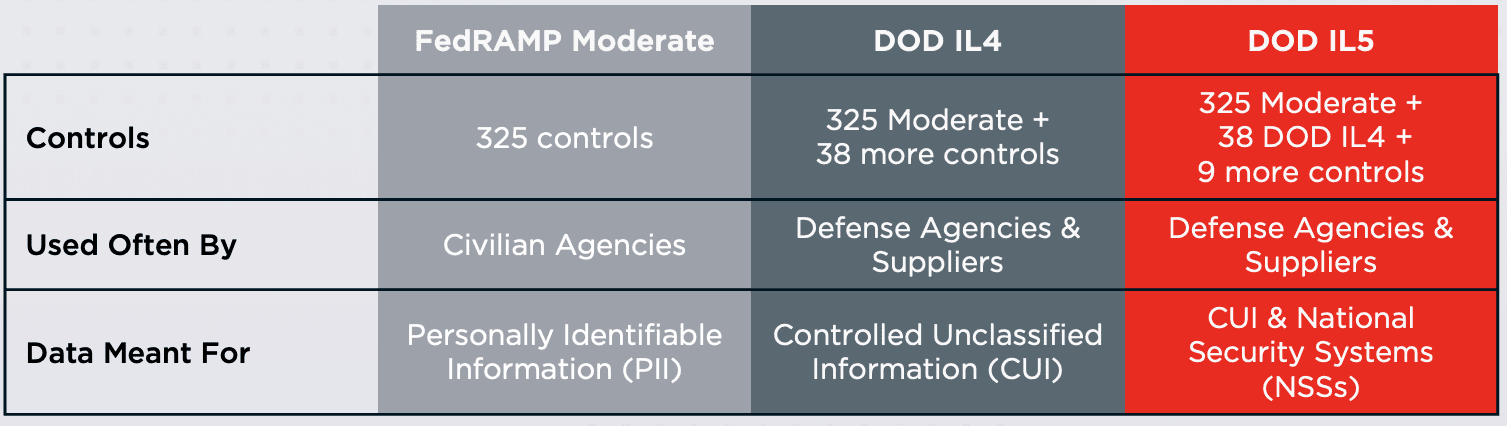
How is DOD IL5 different from DOD IL4 or FedRAMP Moderate Controls?
The main differences between DOD IL4 and DOD IL5 controls are the level of security required for protecting sensitive information and mission-critical systems.
While IL4 controls are designed to protect non-mission-critical, but still sensitive, unclassified data, IL5 controls are designed to protect data that is deemed mission-critical, including data that could potentially result in the loss of life, catastrophic damage to national security, or grave damage to the DoD's ability to conduct its operations.
DOD IL4 controls utilize FedRAMP moderate controls as a baseline, and add additional DOD-specific controls for enhanced security specific to DOD operations. DOD IL5 and even more controls deemed necessary for the protection of NSSs and the highest level of security for CUI.
Why bother with DOD IL5 Controls?
DOD IL5 ICAM is the Gateway to the Rest of IL5 Mission Criticality
Over the past decade in government cybersecurity, ICAM has become more and more consolidated. The security principles behind this are sound: reducing your attack surface with SSO and centralized authentication provide agency-wide policy compliance. A consequence of this trend, however, is that bad actors can more carefully target consolidated ICAM.
And bad actors are realizing the potential for lateral attacks with compromised credentials. Almost half of credential phishing attacks target government employees. If your agency requires IL5 applications or an IL5 environment for your system, but your ICAM is only IL4 compliant (or lower), you’re leaving vulnerabilities open for bad actors to exploit.
Put simply, a DOD IL4 or FedRAMP moderate-tailored ICAM offering won’t meet the cut for IL5 mission criticality. DOD IL4 ICAM isn’t the secure gateway necessary for the highest level of CUI control and NSSs.
Don’t Undercut Other DOD IL5 Investments with Fewer ICAM Controls
With more controls comes more cost. DOD IL5 requires extensive security protocols, including continuous monitoring, advanced access controls, and data encryption. If your organization’s ICAM doesn’t have those security controls, the other security investments you’ve made aren’t being realized.
There is a tried and true security edict: your system is only as strong as its weakest link. If your organization has DOD IL4 ICAM, your DOD IL5 investments aren’t reaping the security benefits and requirements they should be.
DOD IL5 Future Proofs Data Proliferation Concerns
Data proliferation continues to be a significant concern for the DOD due to the increasing volume and complexity of data generated by modern military operations. This data includes sensitive information about military operations, personnel, and equipment, as well as data from weapons systems and other critical infrastructure.
With the proliferation of data comes the need to manage and protect it in a way that minimizes the risk of unauthorized access, manipulation, or theft.
Not only is more and more data being generated, new information is constantly requiring higher levels of classification. DOD IL5 ICAM gives your organization the controls needed to future proof data proliferation concerns across your agency.
Deploy DOD IL5 ICAM with Ping Identity
DOD IL5 ICAM gives your organization the controls needed to balance the requirements to share data across military organizations and mission partners with the need to protect sensitive information from potential adversaries.
We’re immensely excited to add another deployment option to Ping’s solutions for government including existing support for DDIL, Air-gapped, on-premises and hybrid environments. Learn more about how you can modernize defense ICAM with Ping’s government solutions today.
Start Today
Contact Sales
See how Ping can help you deliver secure employee, partner, and customer experiences in a rapidly evolving digital world.


