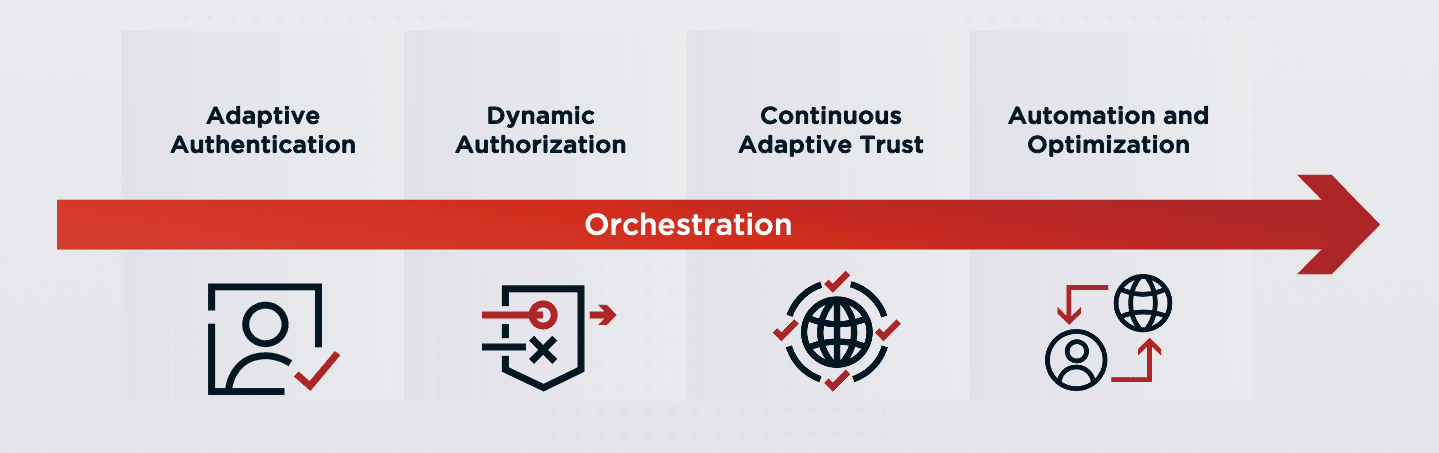
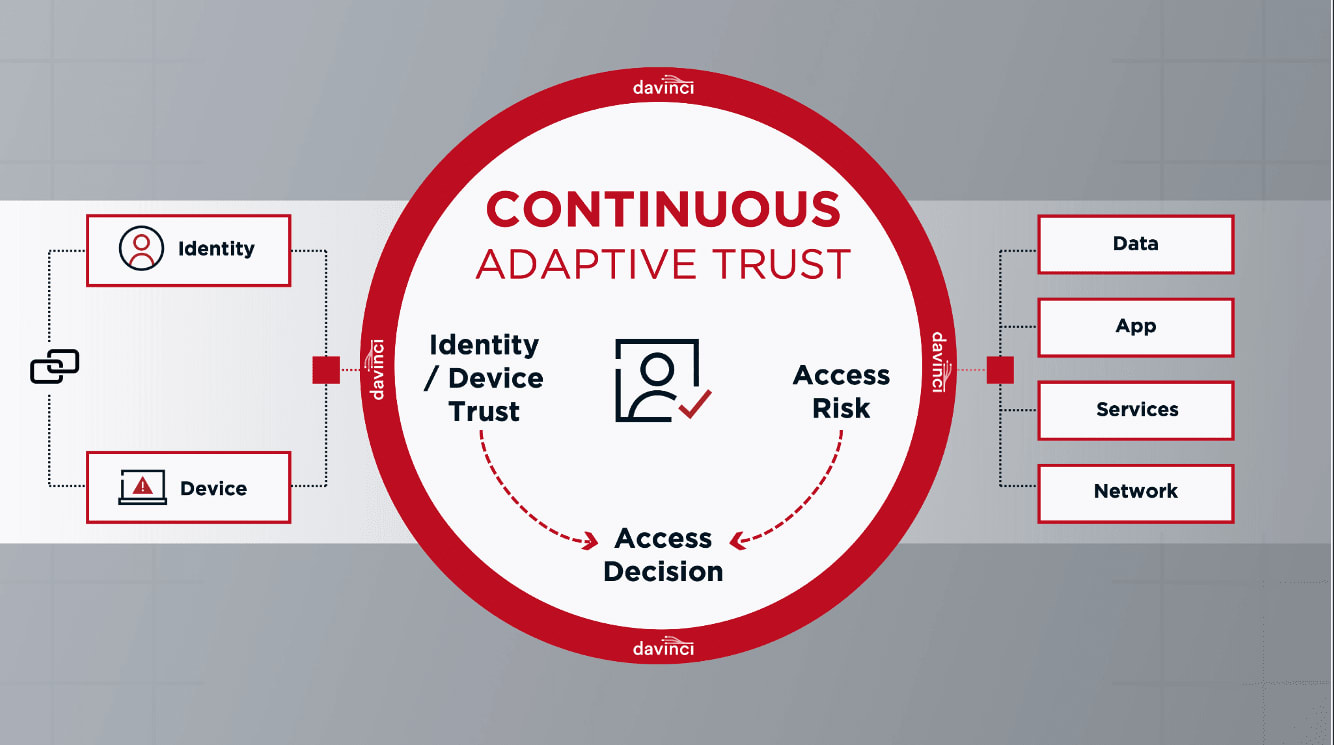
Since the term ‘Zero Trust’ was coined back in 2010, Zero Trust has become the de facto cybersecurity industry paradigm. And for good reason - understanding security broadly through the lens of trust in users ultimately better protects your organization’s resources.
But Zero Trust is a journey: one that hinges upon how well you can truly evaluate trust in a user when handling their access requests day in and day out. Continuous Adaptive Trust is the key step to achieving Zero Trust Architecture. Moving to a model of Continuous Adaptive Trust, one where trust in users is repeatedly evaluated and reevaluated, is worth striving for in the journey towards Zero Trust with best-defined trust with users for user protection.