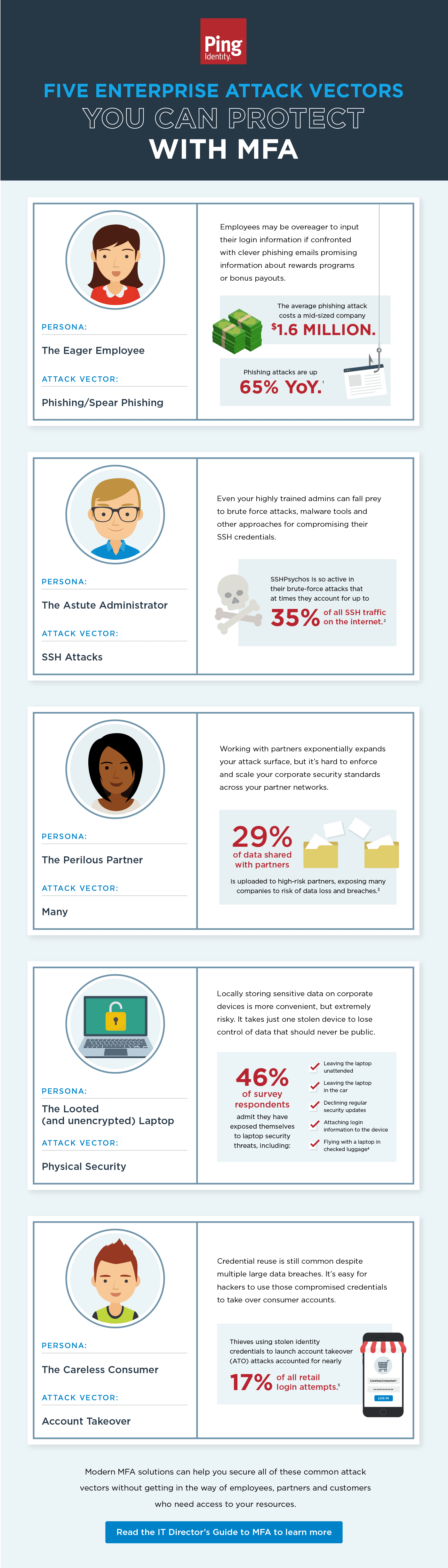
Introduction
Bad actors are always looking for opportunities. From rogue insiders to hostile nation states, vigilance is required to prevent hackers from exploiting vulnerabilities that act as a gateway to your network. For example, the recently publicized vulnerability in the widely used Log4j code offered hackers a way to access the servers of countless organizations.
The pandemic increased awareness of the challenges organizations face in identifying and protecting their entire attack surface to prevent data breaches. More and more organizations are turning to the identity-centered Zero Trust approach to security, which assumes that external and internal threats exist on the network at all times.
Read on to learn the difference between attack surfaces and attack vectors, and how to minimize risks to your network.