Let’s explore three use cases that Ping Identity’s financial services customers adopted in 2021 to improve security and their clients’ experience:
Fraud Prevention
Digital banking fraud is a growing threat and more incidents equal increased costs. Criminals gaining access to a customers’ online accounts and making unauthorized transfers grew by 43% in 2020 and cost £159.7m in the UK alone.
Financial services organizations are constantly reviewing the security measures and are now moving from detection to real time mitigation. However, there is broad recognition that this cannot come at the expense of delightful experiences for legitimate customers. To achieve the correct balance, successful organizations are focusing on trust and safety without putting additional security measures on all users.
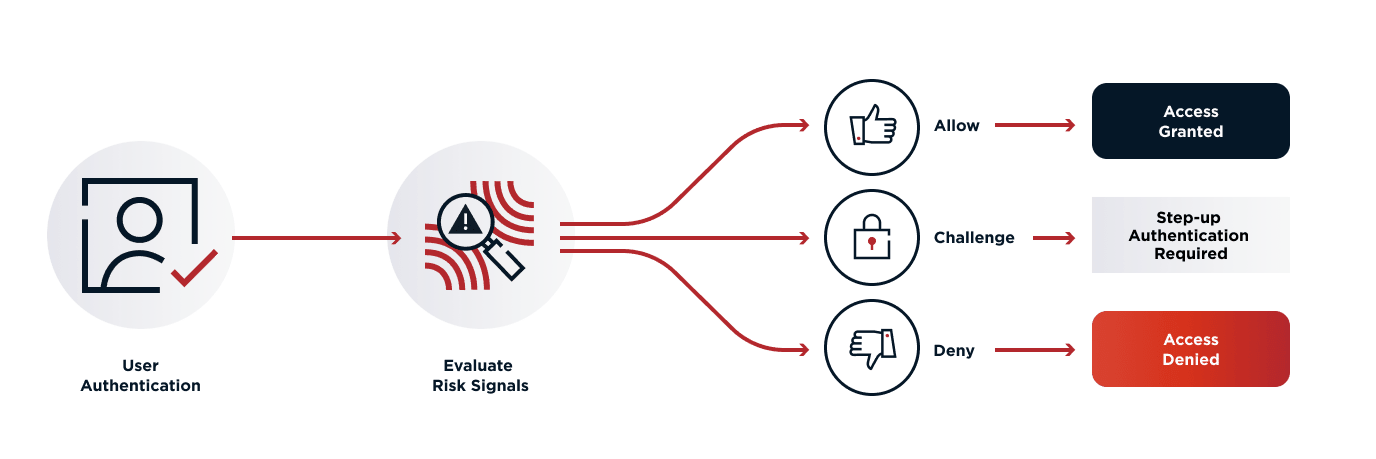
How are they doing it? Establishing trust involves processing a mixture of signals throughout the user’s journey. These signals may come from fraud and risk services, or information about the user, device and action being performed. The user may be directed to different user experiences depending on the trust level (for example, to require MFA for certain transactions if the trust level is low). The intent is to provide an appropriate level of friction for the action that the user is performing.
Dynamic authorization allows fraud team members to assimilate signals from across the organization and craft policies that determine the user journeys for different trust levels. By lifting the authorization policy out of applications and into a shared, centralized user interface, fraud teams can quickly introduce new signals as they become available and experiment with how these signals are applied and enforced against different user journeys. They are no longer tied to slow IT release schedules, which enables them to get ahead of fraudsters as they spot emerging threats. This is allowing financial services organizations to constantly adapt their experiences appropriate to the trust level associated with the individual user.
Consent Management for Open Data Regulations
As consumers adopt digital services, they are looking for mechanisms to use and move their data between services in ways that benefit them. A growing number of consumers are sharing their financial data through screen scraping services to gain access to innovative financial services products. Screen scraping is the automated, programmatic use of a website, impersonating a web browser, to extract data or perform actions that users would usually perform manually, such as Mint.com or Plaid.com that automatically collect banking data on your behalf to present a consolidated view. However, screen scraping presents consumers with security risks as it requires them to share their banking login credentials with third party service providers.
It’s risky to store users’ credentials. Many users reuse passwords across accounts, and breaches can compromise bank accounts and other online accounts. The only way to revoke access is by changing passwords and most people don’t remember which sites and apps they’ve given access to, or what level of access they’ve provided. Furthermore, the user experience and functionality of screen scraping is frequently disrupted when financial services providers make minor system changes.
There is an alternative. Open banking allows data to flow in a controlled way between organizations via an API, letting consumers and small businesses securely and efficiently transfer their financial data among financial institutions and accredited third party service providers. While Open Banking support is further ahead in Europe than the U.S. and Canada, this is changing with the emergence of the FDX specification and the recent Canadian mandate to introduce Open Banking by January 2023.
There are inherent risks to sharing data, and as financial services organizations switch to API-first approaches it is critical to develop governance processes around the privacy and security of personal data. One particular focal area is that the flow of data across open banking APIs must always be subject to express consent. In other words, consumers may be able to control what they share, when it is shared, and to whom the data is available.
To satisfy this, financial services must implement a fine-grained consent record that lets customers control who can access what information. Once a consent record is in place, dynamic authorization can be used to enforce the consent, performing a series of checks against each API request to confirm that the requestor has the appropriate consent to access the data.
PingAuthorize centralizes the consent enforcement function so that it's not embedded separately in every application. This allows the bank to provide a consistent layer of fine-grained authorization across all applications. Ultimately, this provides consumers with a more secure method of sharing their data, reduces the risk associated with screen scraping, and gives them a simple mechanism to control exactly how their data is shared. For the financial services organization, it improves security, visibility, brand trust and business agility. It’s a win-win for everyone involved.
Permissions and Entitlement
Financial services organizations have rules governing who can access what information and who can perform specific operations. In some cases, these rules are defined by applicable laws and regulations or by internal company policies. In other cases, to give customers flexibility and desirable experiences, financial services are creating rules for specific operations to allow customers to delegate access rights to other end users such as employees or relatives.
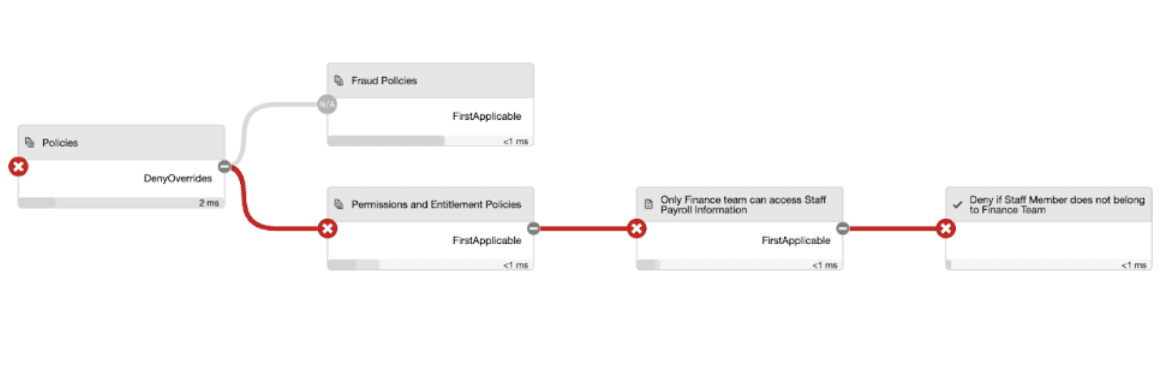
For example, in business banking a payment over a certain amount may require additional approval before processing. A staff member may be able to initiate the payment, but managers must approve them. In retail banking, a member of staff may only access accounts if the customer is serviced by the same branch or region as the employee, or a customer may have access to a minor’s account when they are the legal guardian of the account owner.
Here, authorization is determined by relationships between the user, the resources they are accessing and the action performed. This once meant creating separate role based access control (RBAC) policies to determine permissions for each category of staff and customer but this approach led to an onerous administrative burden around outdated permissions.
Dynamic authorization provides a more efficient solution. Permissions to perform actions on resources are expressed through explicit policies, drawing contextual entitlement information from relevant data stores. The organization explicitly defines relationships between customers, staff, resources and actions, quickly adapting without re-working static RBAC policies.
This creates better information security based around principles of least privilege. It improves user experience where only the objects and actions that a user can perform are displayed, and it gives the business a consistent, visible mechanism to implement the business rules governing access.