The United States Postal Service (USPS) introduced its informed visibility service in 2017. The service allowed for the retrieval of data regarding mail sent by USPS commercial customers. While this was a big step forward for digitization, the API that powered the service included a flaw that inadvertently allowed any logged-in user to view—and in some cases even modify—the account details of other users.
Since the API accepted wild card search parameters, there wasn’t even a need for hacking tools. Literally anyone could manipulate the search using a normal browser and with minimal effort as evidenced by the estimated 60 million people whose personal data was exposed.
According to the analysis done by KrebsOnSecurity, at least some data fields, like email addresses, required an extra validation step before they could be modified by an unauthorized person(s). This makes sense since large commercial customers need some assurance that their account information can’t be modified without an authorization check. But the security flaw was the omission of an access requirement to ensure the identity associated with the request had the appropriate access to read or modify the record.
The vulnerability is best described in the OWASP Top Ten Document as “A5: Broken Access Control.” It could have easily been prevented if the API in question would have done an access check to see if the person making the request had the proper authorization. This same access control check could have been used to filter wildcard search results, too.
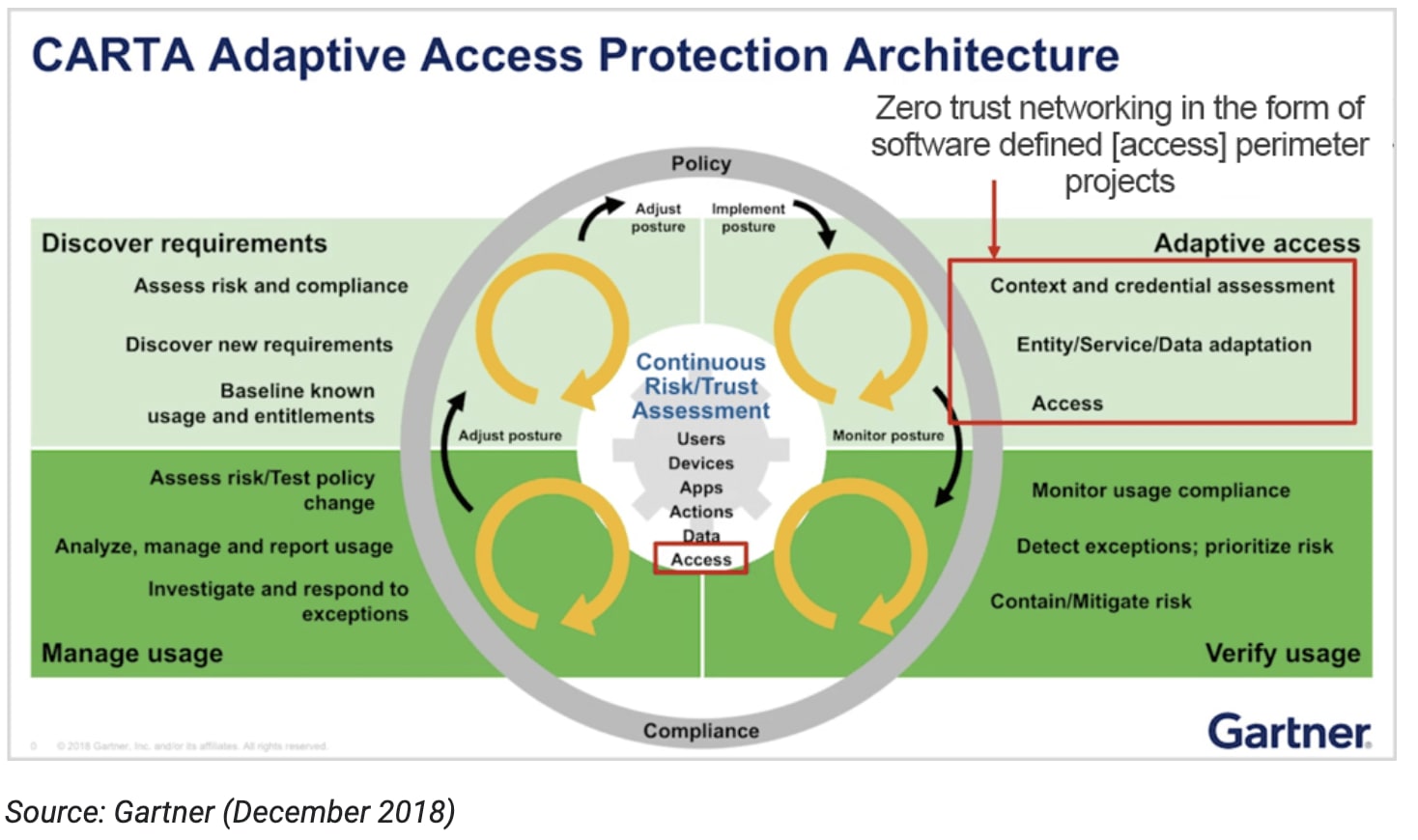
This example also highlights another primary principle of Zero Trust: always verify the permissions and level of risk associated with an individual user at the time of the access request. We call this matching the trust established during authentication against the risk of access.
Since the USPS did require authentication to access the API in the first place, they did one better than First American. Unfortunately, equating authentication and authorization is a common mistake which often results in data breaches like these, where the impact can be outsized.
How to Prevent this Vulnerability
One way to prevent this vulnerability is to have each developer implement authorization checks on a per API basis. But many enterprises prefer to manage and implement authorization centrally.
Using the Adaptive Access Security solution from Ping, these enterprises are implementing a combination of medium- and fine-grained authorization to protect against unauthorized and/or unintentional access and potential data exposure. The solution secures APIs by enforcing an authorization check and filtering the data returned in the request. It does this in accordance with externalized data access policies composed by business users (e.g., security and compliance professionals) in a graphical interface.