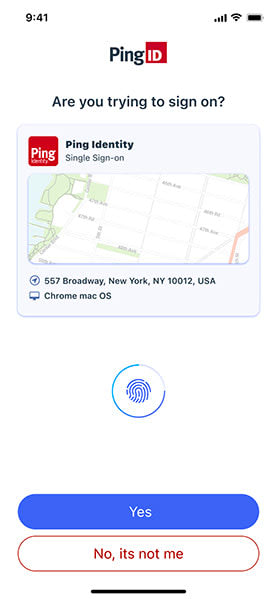
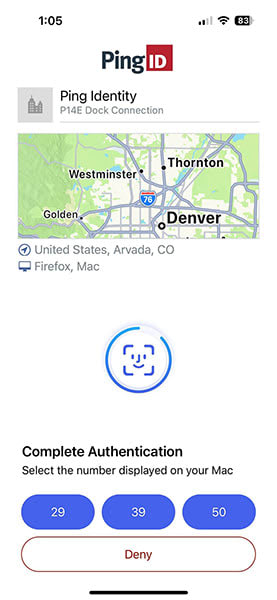
MFA bombing is a tactic, also known as an attack vector, that bad actors use to commit account takeover. Sometimes called MFA flooding, it plays on a user’s emotions by manufacturing MFA fatigue. In essence, attackers take advantage of users by sending rampant push notifications. Many users deny the prompts initially but get annoyed after receiving one every few seconds and eventually approve the request.
How Does MFA Bombing Start?
Fraudsters initiate MFA fatigue and subsequent carelessness in users following a sophisticated order of operations. In order for MFA bombing attacks to be successful, the following events must take place:
User Credentials & Information Are Collected
As is commonly seen with online fraud, the MFA bombing attack process begins with compromised login credentials. Today’s shrewd and methodical fraudsters have developed a number of effective ways to steal people’s usernames and passwords. Sometimes cybercriminals purchase stolen identity data from other fraudsters. In other instances, they might acquire user credentials themselves by way of scams like social engineering or phishing attacks.
Stolen Credentials Are Used to Send MFA Push Notifications
With compromised usernames and passwords in hand, fraudsters then target an online service known to use push notifications for MFA. Interestingly, the goal here isn’t to circumvent MFA barriers, but rather create a situation where a user is overwhelmed by the very push notifications that are designed to protect them.
The actual attack occurs when the fraudster attempts to log in to a user’s account. Some fraudsters send a few notifications a day so as to not cause alarm, while others overwhelm users with a rapid-fire succession of login attempts. Since they can be extremely disruptive and annoying, mobile push notifications are the most effective tool for fraudsters.
The criminal continues with login attempts until the user authenticates simply to stop the incoming notifications. Once the victim verifies their identity, the fraudster then has free access to sensitive materials that lie beyond MFA barriers.
How Does MFA Fatigue Happen?
Sometimes, as a means to an end, people will engage in behavior that they know is borderline unsafe. Who amongst us hasn't disabled a smoke alarm to make the low-battery alert stop its intermittent screeching? MFA fatigue attacks rely on similar human impulses, which ultimately make users vulnerable to MFA bombardment.
With MFA prompt bombing, attackers attempt to get access to an account or device by flooding a user's authentication app with push notifications. As mentioned above, some attackers send a few push notifications a day thinking they will fly under the radar, while others bombard the user with continuous messages, but the intended outcome in either approach is the same: to get users to authorize access in order to make the notifications stop, thereby granting access to the attacker.