FIDO is an open standard that enables users to authenticate via a highly secure cryptographic login, which is phishing resistant and easy to implement. FIDO2—the latest protocol—leverages users’ physical devices to store credential information locally on secured hardware and sign authentication challenges.
The joint announcement by Apple, Google, and Microsoft to support passwordless is a clear statement that FIDO is the way to move towards a passwordless future, making it the new standard.
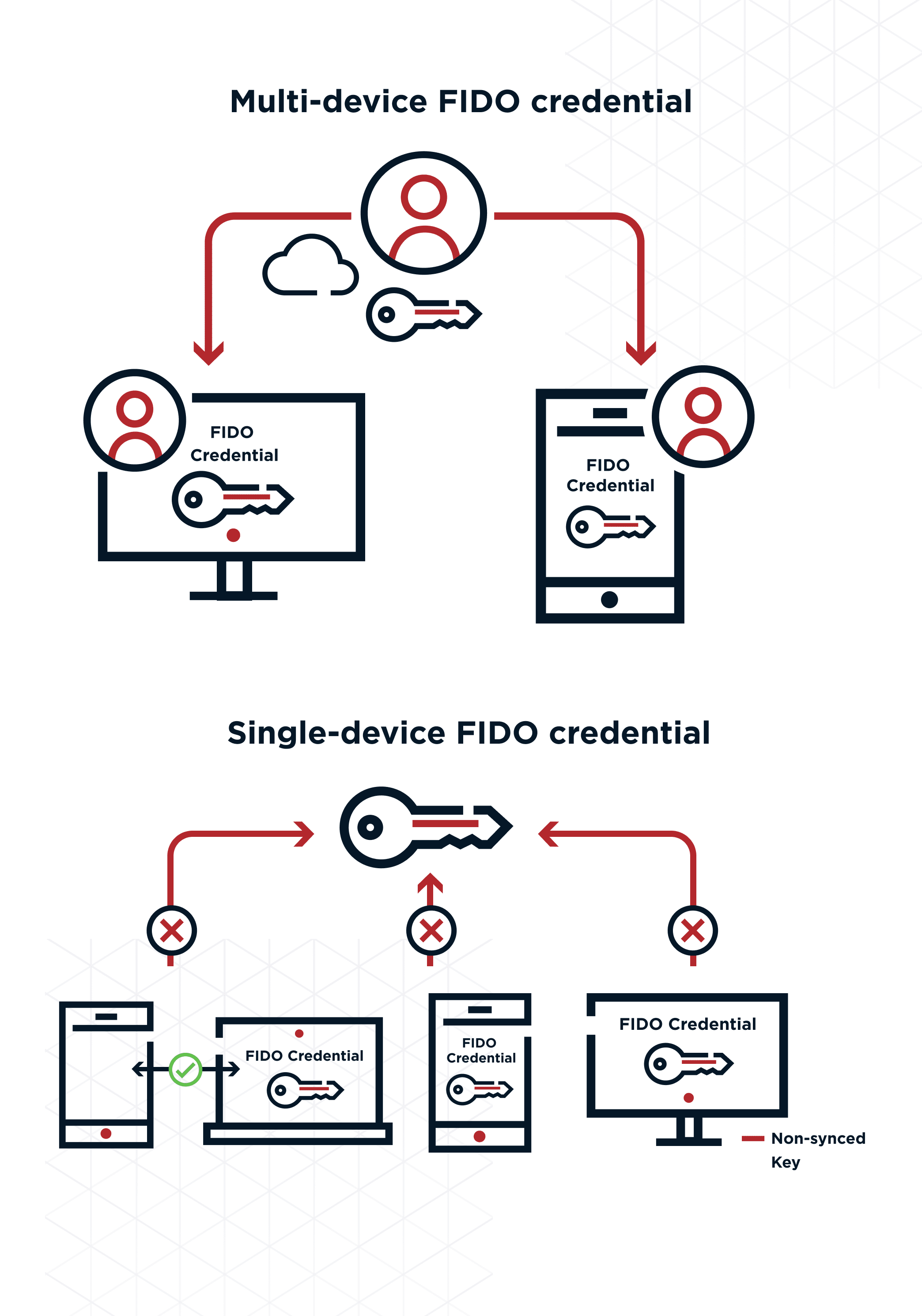
Passkeys remove the most common barriers to FIDO adoption by (1) enabling users to enroll to FIDO once, sharing the credential between devices on the same platform, and (2) being able to leverage registered FIDO devices on one platform to authenticate when logging in from another.
Getting here wasn’t without some challenges. Let’s back up a little bit to see how we got to where we are now.
Initial Headwinds with FIDO Implementation
As a cryptographic solution that is both domain-bound and hardware-bound, FIDO has a reputation as an innovative approach for replacing password-based logins with fast, convenient, and secure login experiences across websites and applications.
However, even as FIDO authentication broke new ground in the use of passwordless, there were some initial setbacks that needed to be mitigated before major enterprises would announce their support for passwordless and before it would catch on broadly with consumer and workforce users.
Here are some of those setbacks:
Registration and Usability
One of the initial problems with FIDO was that it still relied on weaker authentication mechanisms (like passwords) during the initial registration process. The first time you would register a FIDO device, you would need to bind your user authentication to that device.
This meant that if you tried to log in from another device that you owned, you would first have to authenticate yourself using an alternative method (again, most likely going back to the password) before the site or application would give you access. Then, once approved, you would need to register that new device as well to leverage FIDO on that device thereafter. This process would have to repeat on each of the devices you used for access.
It’s easy to see how FIDO’s use became tedious, discouraging organizations from giving up traditional passwords and familiar login experiences — despite their known weaknesses — in exchange for something representing only a slight improvement.
Failure to Fully Eliminate Passwords
Broadly speaking, there are three stages of password elimination:
- Password used in combination with other credentials to authenticate
- Password obscured from users but exists at backend (user may need to revert when running a recovery flow, for example)
- Password completely eliminated
Considering the issues with registration, FIDO only really made sense in one circumstance. For FIDO to fulfill its vision of completely phasing out passwords and eliminating the threat of common password attacks, it needed to be fully adopted as the only way for users to authenticate. In other words, the act of continuing to mix in traditional password login methods presented a barrier that ultimately led organizations to delay their adoption of passwordless.
Recovery
Furthermore, the failure to fully eliminate passwords led to recovery problems. To illustrate, organizations that pursued FIDO as the only way for their users to authenticate ended up facing issues with user account recovery. As a result, users ended up needing access to at least two previously registered FIDO devices — in case they lost one — to enable account recovery.
Otherwise, in the absence of the only FIDO-registered device that their identities were bound to, they’d be unable to access any of their accounts.
Slow Adoption
From the friction during registration to the account recovery issues resulting from the need for back-up FIDO devices (in the event of a lost FIDO-enabled device), it was hard to see the benefit that FIDO would bring to organizations and their users. This turned out to be a significant deterrent to broad adoption of FIDO.