Federation
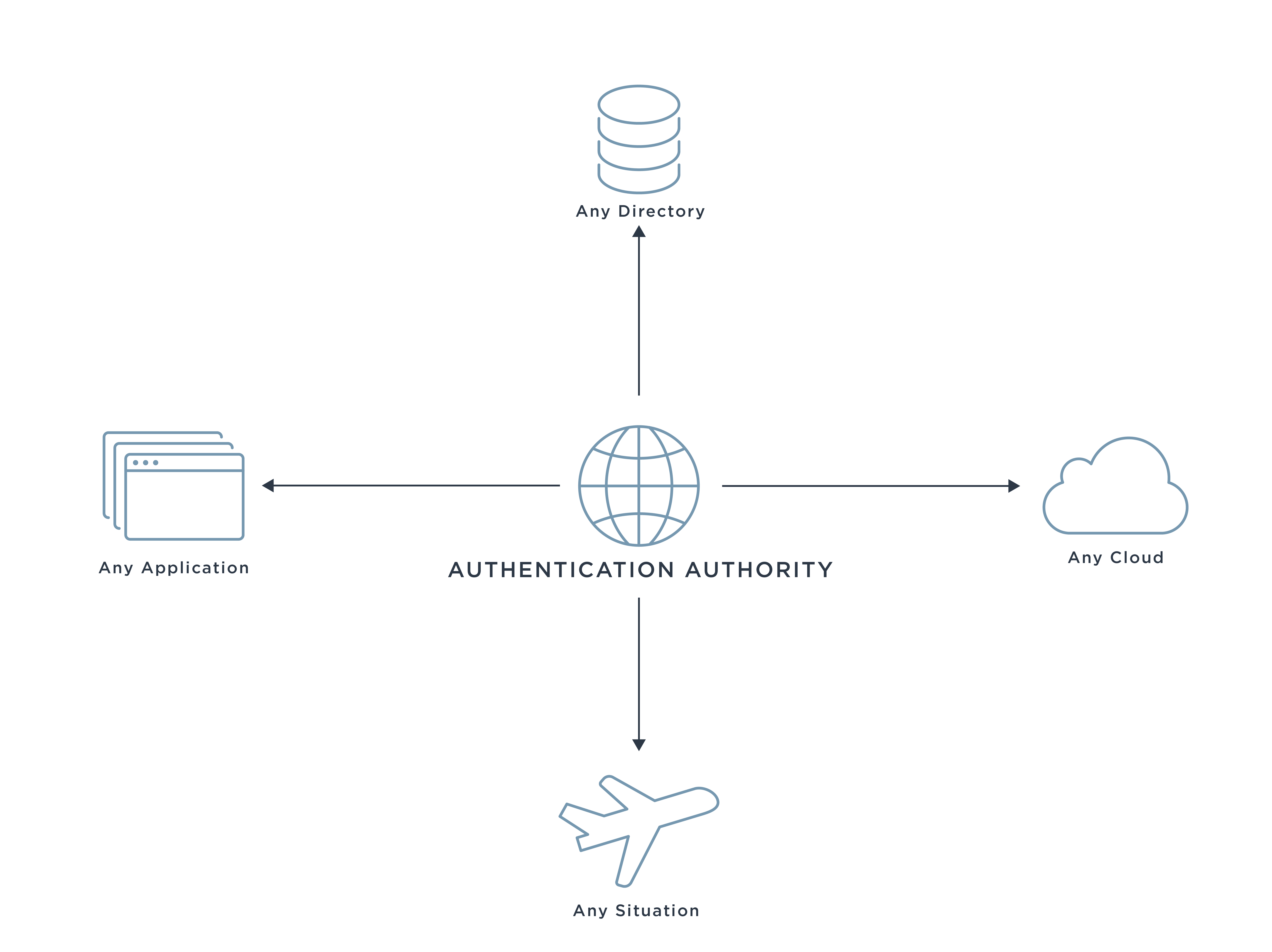
Federation consists of the “technology, policies, standards, and processes that allow an agency to accept digital identities, attributes, and credentials managed by other agencies.” To enable federated identity activities like user authentication and single sign-on (SSO), organizations need a federation server.
Customers rely on PingFederate, an enterprise-proven federation server, to accomplish these activities through key capabilities like:
Standards-based signed assertions
Adaptive authentication policies
Pre-built adaptors and integrations
PingFederate also supports existing ICAM authenticators without requiring re-enrollment.
Considerations When Choosing a Federation System Component
While every ICAM component is important, it’s especially critical to do your due diligence when it comes to federation. As stated within NIST SP 800-63: “federation is a keystone in the ability to enhance the privacy of the federal government’s constituents as they access valuable government digital services.”
This is because federation is essentially the working arm that brings everything in the digital identity guidelines together. To put it simply:
800-63A, the enrollment and identity proofing requirements, makes attributes available for use.
800-63B, the authentication and lifecycle management guidance, makes credentials available for use to validate an identity against.
800-63C, the federation and assertions guidance, is where the actual process occurs to issue the credentials from 63B to access the attributes from 63A.
So federation is what provides the results of an authentication. This step is so important that NIST is working on additional guidance, 800-63D, to ensure that agencies can align their federation with international specifications, like SAML profiles, to enhance interoperability.
And again, this isn’t about ripping and replacing your entire infrastructure. A robust federation hub will be able to bridge older authentication sources, multiple standards and modern applications to provide secure access for all users in a quick, cost-effective manner. So long as you employ modern federation capabilities, you can still leverage your existing investments.
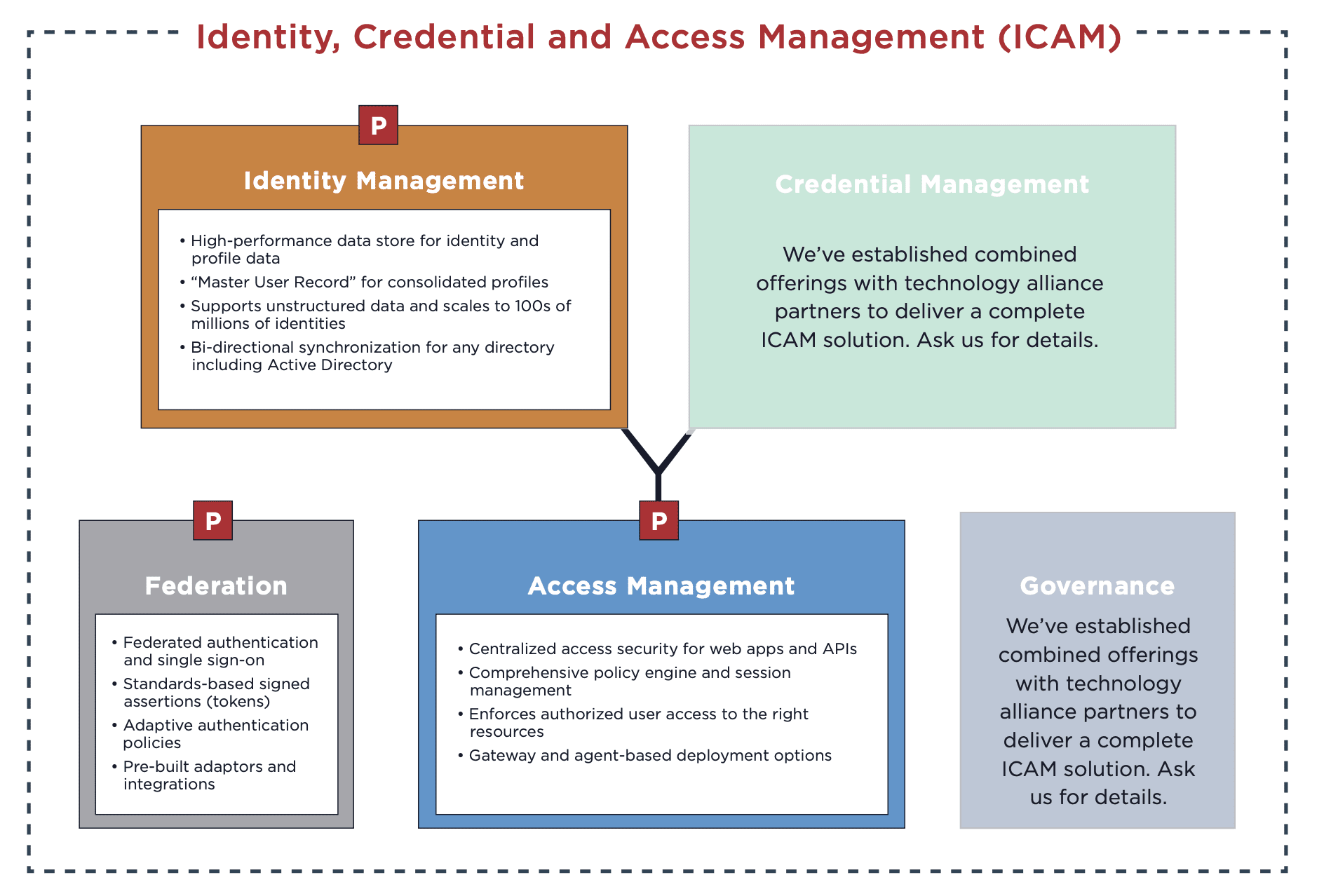
Identity Management
Identity management is how “an agency collects, verifies, and manages attributes to establish and maintain enterprise identities for employees and contractors.” By providing a high-performance data store for identity and profile data, our identity management component is able to:
Support unstructured data and scale to hundreds of millions of identities
Perform bi-directional data synchronization for any directory, including Active Directory and Azure AD
Create and maintain a master user record for consolidated profiles
This means that all identities can be consolidated to provide a single source of truth across the enterprise for authentication to current and future corporate resources, whether on premises or in the cloud. This is enabled by our unlimited directory integrations and bi-directional syncing capabilities, which let you build a unified profile from multiple sources, so your existing investments don’t go to waste.
Considerations When Choosing an Identity Management Component
Whether you already have an identity management component in place or need to acquire a new one, it’s important to understand how it will enable the flexibility, security and performance you need for identity management.
Many multi-purpose and legacy LDAP databases are unfortunately unable to satisfy these requirements, increasing the risk of breaches, performance lags and outages. Not only can modern options decrease these risks, but they can also do so in a more cost-efficient manner, so you can focus your financial resources on other mission-critical activities.
For example, by leveraging out-of-the-box integrations with legacy and modern applications, you can spend less time customizing and onboarding new applications. Additionally, you can reduce your directory hardware footprint while simultaneously upgrading your infrastructure for better performance and scale.
Credential Management
Credential management is how “an agency issues, manages, and revokes credentials bound to enterprise identities.” With our integrations, customers can uplevel their credential management components to:
Easily integrate with PIV credential service provider solutions
Delineate between PIV and derived PIV
Support cloud authentications (e.g. Google and Microsoft) as well as currently deployed OTP solutions
Considerations When Choosing a Credential Management Component
A quality identity management provider will be able to recommend complementary technologies that are standards-based and can plug into your existing infrastructure. If you need a recommendation, drop us a line, and we’ll be happy to connect you with one of our trusted partners.
Access Management
Access management is how “an agency authenticates enterprise identities and authorizes appropriate access to protected services.” Our access security component, which supports both gateway and agent-based deployment options, elevates this ICAM capability by:
Enabling centralized access security for web apps and APIs
Offering a comprehensive policy engine and session management
Enforcing authorized user access to the right resources
Considerations When Choosing an Access Management Component
Some organizations have legacy WAM systems built to protect on-premises applications but not those hosted in the cloud. Without a solution to protect those cloud assets, agencies could experience disconnected, uncoordinated policies and sessions—an unnecessary risk.
Upleveling access management capabilities is even more critical following the President’s May 12th Executive Order (EO), which instructs the federal government to “accelerate movement to secure cloud services, including Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS).”
Within 60 days of the EO’s publication date, every agency needs to update their plans for how they’re going to increase their adoption of cloud technologies. When thinking this through, be sure to consider if your existing access management components provide the capabilities necessary to protect these new technologies you’ll soon onboard.
Governance
And last but not least, we have governance, which is the “set of practices and systems that guides ICAM functions, activities, and outcomes.” This includes rules to help manage access and risk, continuous analytics to determine if inappropriate access has been attempted and mitigation capabilities to resolve any confirmed issues.
We partner with a number of governance providers, as well as providers whose tools consume governance data for further security uses, such as security information and event management (SIEM) platforms. Let us know what you need, and we can make a recommendation.
Considerations When Choosing a Governance Component
Similar to other technologies mentioned above, the recent EO is accelerating the need to enhance governance capabilities. Specifically, the President has given the Secretary of Homeland Security 60 days from the date of the order’s publication to create a cloud-service governance framework. As this framework is developed and shared with the public, it will be vital to ensure your governance component provides the capabilities necessary to meet these new requirements.