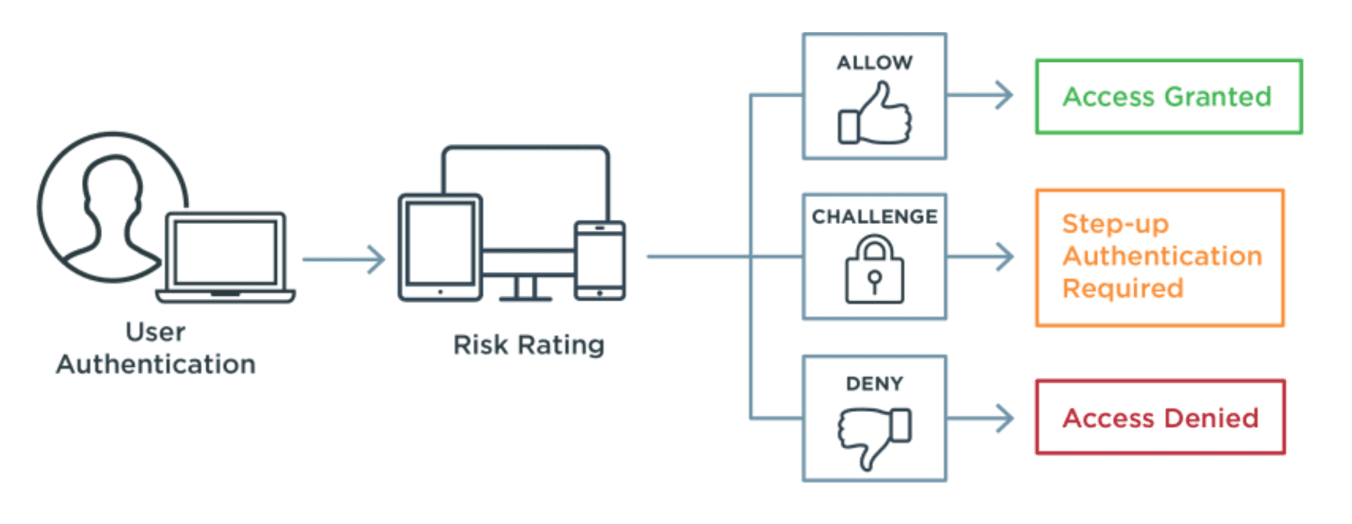
There are numerous methods a bad actor can use to get the credentials needed for account takeover, in addition to data breaches or buying them on the dark web. Account takeover fraud methods include:
Phishing
Phishing schemes, often conducted via email or text, are designed to get victims to provide account information to fraudsters. This type of social engineering is characterized by tricking victims by impersonating legitimate organizations, like government agencies and banks, or victims' family and friends. We've all gotten emails or texts from "banks" saying our accounts are locked and we need to provide login information for account recovery. Or "friends" who ask us to click on a link, which will install spyware or other malware on our computer or mobile device. Victims who unknowingly fall for these types of fraud provide bad actors with easy access to their accounts.
Phishing goes beyond these classic schemes and continues to evolve with the help of AI-assisted tools. Recent advanced phishing tools apply the more advanced Adversary In The Middle (AITM) attack, which is even resistant to some MFA methods such as OTP.
Phone Scams
Seniors are often the target of phone scams, since they may have listed phone numbers, own a home and have savings and good credit. Seniors with dementia or other challenges are at higher risk of fraudsters repeatedly taking advantage of them. This form of social engineering is perpetrated by scammers pretending to be tech support in need of access to the victim's computer or a grandchild who needs banking information in order to transfer funds for an emergency. The FBI estimates elder fraud results in $3 billion in losses annually.
Unsecure WiFi
Personal WiFi needs to be secure, which may require changes to default settings. The same is true of security settings on Internet of Things (IoT) devices that use WiFi, like doorbell, thermostat and garage door apps, which can be hacked and allow access to a network. Public WiFi should never be used for anything important, especially when it involves logging into accounts. A bad actor can set up a man-in-the-middle attack by creating a fake wireless access point in a public location, like a coffee shop, and use it to intercept your internet activity.
Credential Stuffing / Password Cracking / Brute Force Attacks
Credential stuffing uses bots to test compromised credential combinations on multiple websites or apps to access accounts. Password cracking tools automate the use of leaked or stolen usernames with dictionaries of common passwords, sometimes supplemented with custom dictionaries, to access accounts. Brute force attacks are a popular cracking technique that involve trying different variations of symbols or words until the correct password is figured out.
Session Hijacking
Authenticated user sessions are maintained by storing a session and authentication token on the client device (e.g. cookie in the browser). Attackers may bypass the login and take over an account by stealing a valid token. Stealing a token may be done using different techniques such as Man-In-The-Middle (MITM), Man-In-The-Browser (MITB), and others.
Rise of AI in ATO Fraud
The rapid developments in artificial intelligence are changing the fraud landscape as both attackers and those who fight to stop them are leveraging AI to be more effective. Fraudsters use generative AI to create more accurate and convincing social engineering campaigns at a large scale, developing phishing emails, scam texts, and scripts. Generative AI can also be used to create realistic voice and video fakes, and may be utilized to fake identities and identity documents in an attempt to bypass identity proofing. Meanwhile, counter-fraud tools also leverage AI, creating more accurate AI models using recent technological breakthroughs and leveraging LLMs as part of the fraud analytics process, offloading some of the human labor involved in fraud analysis. This makes finding the right fraud prevention team and tools so important in 2024 and beyond.