In today’s digital world, the number of applications an enterprise manages continues to increase. Managing all of those applications and which employee has access to which app can be complex. That complexity only gets compounded as your enterprise grows, people switch roles within your company, or employees go elsewhere.
Today, we’re excited to announce that Ping Identity supports a new feature in AWS Identity and Access Management (IAM) that gives your administrator some relief when it comes to managing access to AWS resources.
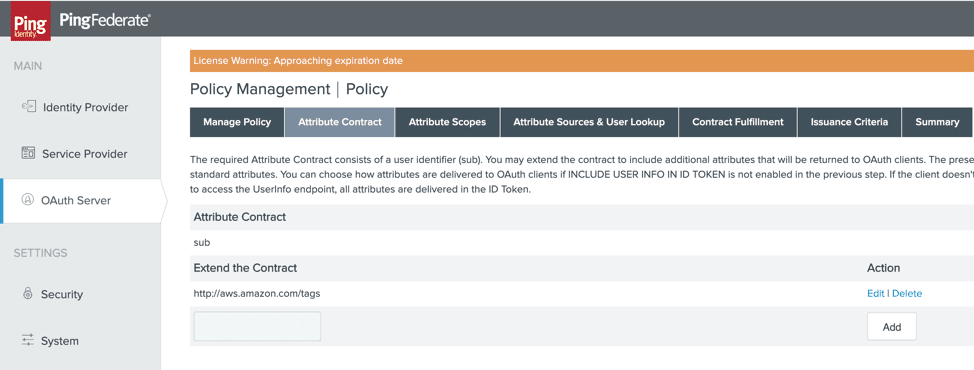
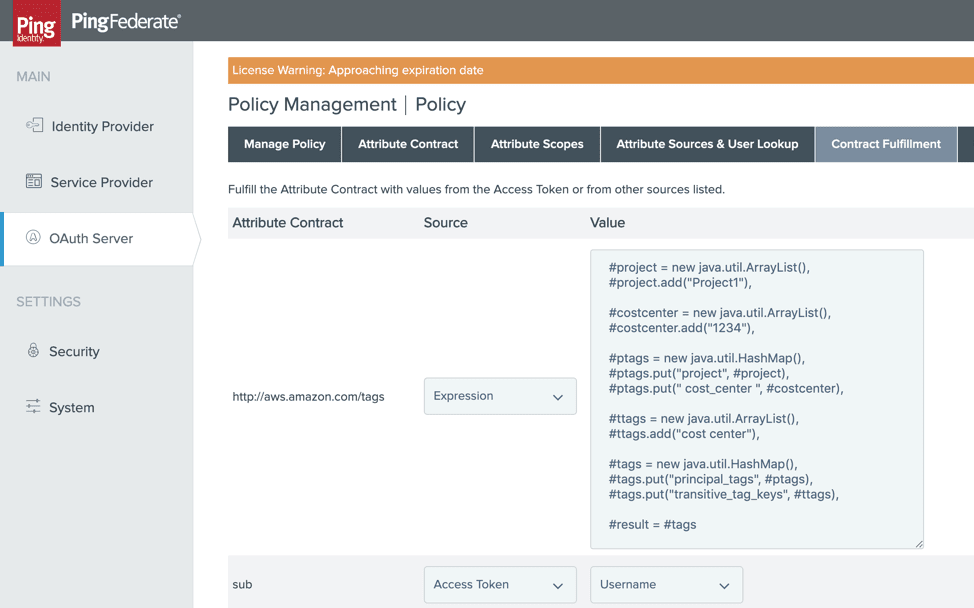
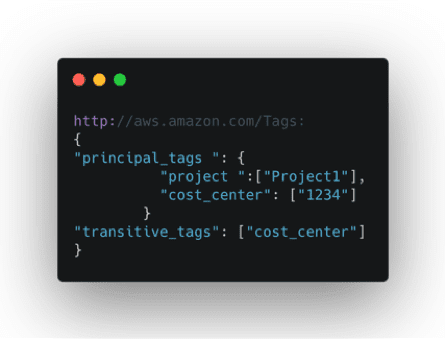
With AWS’s IAM recent launch of session tags, now enterprises can use Ping Identity for attribute-based access control (ABAC) in AWS. ABAC helps today’s enterprise simplify fine-grained access to AWS resources by using attributes from their own corporate directories in permissions rules.
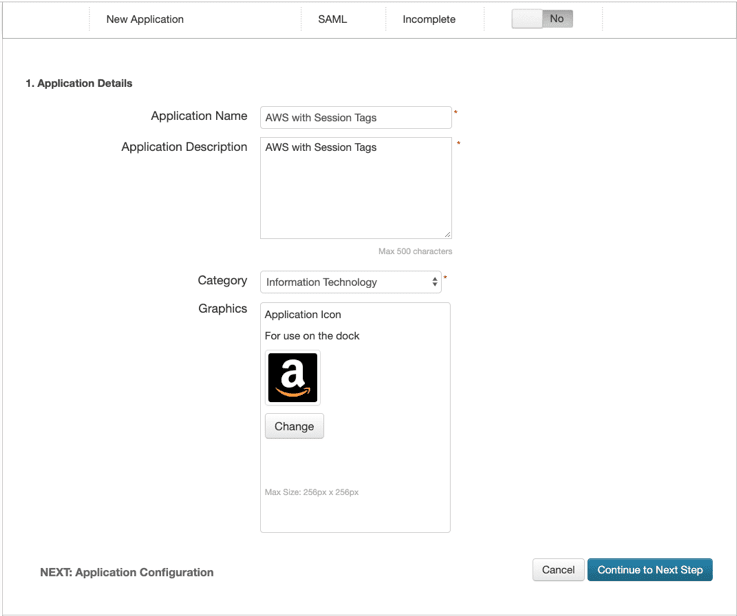
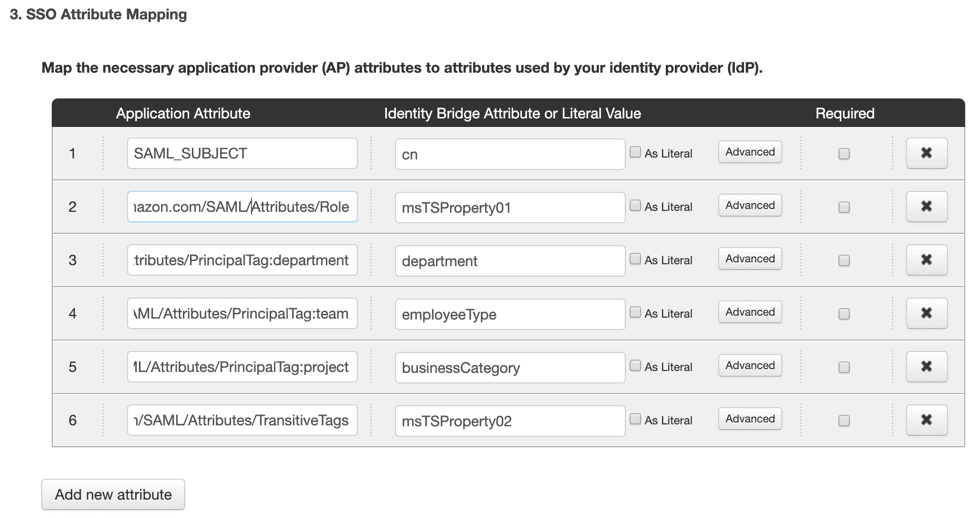
Read on to discover the value of AWS session tags, explore a real-world example, and learn how to configure PingFederate and PingOne for Enterprise to take advantage of this new AWS IAM feature.