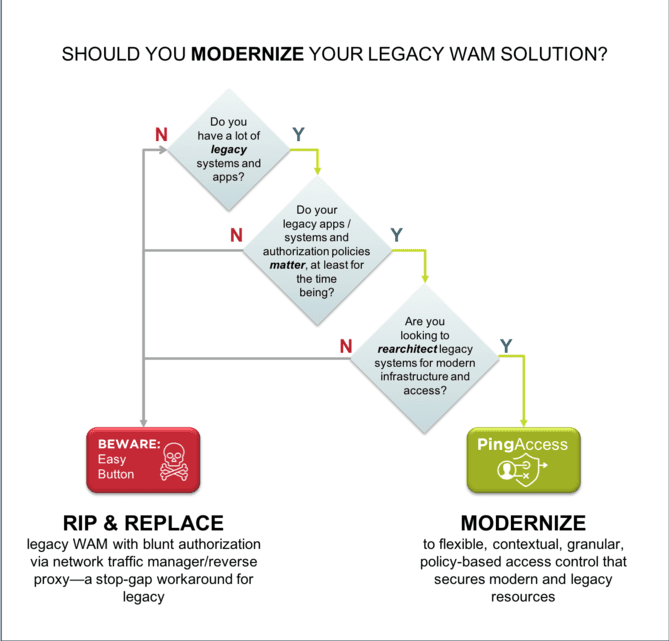
At Ping Identity, we’ve seen it all. Having worked with the largest, most complex global enterprises, we know that “rip and replace” is never an option when you’re dealing with a delicate web of proprietary connections between your legacy WAM system and your enterprise’s critical applications, and changing even one thing could upset a fragile IT ecosystem.
Three proven ways to ease your migration challenges are:
- using policy migration tools,
- leveraging Ping’s Professional Services teams to help plan and guide the way, and
- taking advantage of Ping’s world-class partner ecosystem.
1. Policy Migration Tools
Ping’s technology solutions and tools include token translators and policy migration tools to enable coexistence and avoid downtime disruption. If you are currently using common, outdated WAM systems like CA Single Sign-On or Oracle Access Manager, PingAccess Policy Migration (PAPM) is a software tool that consumes a policy export from those systems and helps automate the tedious, error-prone manual process of translating existing legacy access policies into modern PingAccess policies.
Migration Steps with PingAccess Policy Migration
Here are the basic steps to migrating off of a legacy system using PAPM:
- Before initiating PAPM, set up PingFederate (PF) and PingAccess (PA) environments and create standard, modern application configurations. You’ll use these as the basis for policy groups.
- Use PAPM to consume a policy export file from your legacy WAM system and convert it into PingAccess JSON objects.
- Establish read/write connection to PF & PA environment settings via admin API.
- Look to your standard PF & PA application configurations to create a set of policy groups to which you will map legacy policies.
- Onboard each application, selecting the appropriate policy group for the authentication requirements of that resource.
Useful Beyond Migration
Once you’ve gotten through the process of migrating/translating your policies, PAPM also enables you to test the outcome of a policy before it is live by allowing you to impersonate different logins, test authentication and OIDC flows to applications prior to agent and app configuration, and conduct load testing to measure a policy’s response performance.
Another important capability allows you to automate the promotion of a policy between environments you define (e.g., dev, test, prod), with a side-by-side view of different policy exports so you can easily see what has changed between versions.
And last but not least, even after you’ve successfully coexisted with your legacy system through a seamless migration and you’re ready to sunset it, you can continue making use of PAPM’s monitoring capabilities. This lets you view real-time environment health status indicators for PingFed and PingAccess servers, alerts administrators to issues, and displays indicators for historical/live response times, CPU utilization load, open proxy connections comparisons, available memory usage, sync status, etc.
2. Professional Services
For most of the solutions in Ping’s Intelligent Identity Platform, deciding to buy is one of the very first milestones of a journey to modern access management. Often, our products are not being implemented in green field use cases. Instead, the reality for many of our product implementations is that Ping’s capabilities will be coexisting with or migrated off of another legacy IAM system. Some organizations choose to manage their own migration approach with an internal project team if they have the resources and expertise in-house. Many other organizations choose the approach of bringing in outside experts, and their first stop is often Ping’s own Professional Services team or one of our experienced partners.
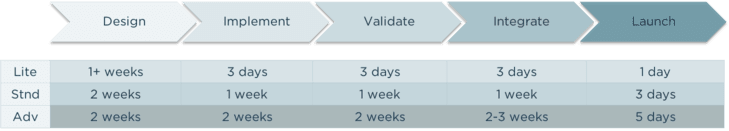
Specifically for enterprises looking for a headstart to get a high-speed MVP instance of PingAccess in place, the Professional Services team offers a PingAccess Implementation Accelerator. This is a comprehensive service to deploy a scalable and performant PingAccess with a limited number of environments and applications over a structured amount of time. Once the initial deployment is complete, then additional bespoke services can be defined as needed to help with the ongoing work to fully migrate from the existing platform.
PingAccess Implementation Accelerator - Delivery Approach
In addition to this out-of-the-box, outcome-based professional services package, other organizations that are more proficient and prefer to “drive” have benefitted from modular Advisory Engagements, where our professional services team is engaged to do just one piece, such as architecture and design, or for regularly scheduled Q&A sessions throughout the implementation cycle.
3. World-class Partner Ecosystem
Working with our partners, we’ve successfully enabled dozens of complex enterprises to modernize from a legacy WAM system. For enterprises looking for a flight plan to “de-risk” the transition, one solid option is to enlist expert help. Just one example: KPMG has outlined a proven approach to delivering PingAccess enterprise implementation projects, automating the process and successfully migrating, testing and promoting hundreds of applications into production. And their expertise and approach is proven, even for the most complex enterprises: Jeff Richardson, SVP of IAM for Bank of America, chose to migrate to Ping Identity’s solution working with KPMG to implement PingAccess.
The Ping Global Partner Network is more robust than you might expect, given the high amount of capabilities and services overlap within identity and access management. Our philosophy is that today’s winning businesses don’t go it alone—playing nicely with other leading companies in both technology and services is part of our DNA with open standards, and this carries over into how we really see partners as the key to serving enterprise customers the best way possible.
Beyond helping you plan, implement and optimize your PingAccess implementation, our professional services team is also a direct line to our extensive partner ecosystem. When your needs exceed the capabilities of our products, our partners are there to make sure no challenge is left unaddressed. Using our partner directory, you’ll likely find implementation and delivery partners who specialize in migrating off of your specific legacy system or integrating with other key technologies you have in place.